HackTheBox - Blocky

Starting with a basic port scan with nmap automator
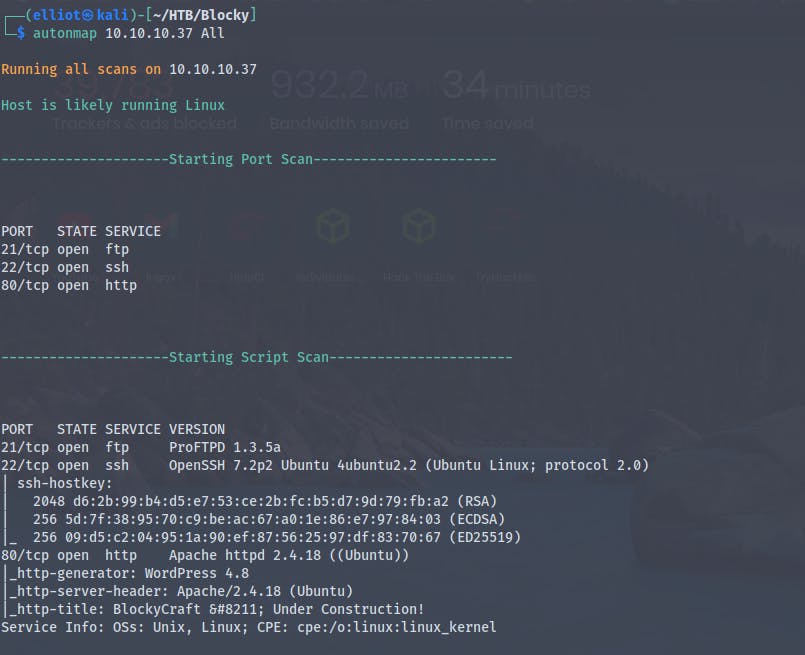
We have a web server running on the port 80

We see that the website is running wordpress and we have no vulnerable plugins or themes installed and we also get a username
┌──(elliot㉿kali)-[~/HTB/Blocky]
└─$ wpscan --url http://10.10.10.37 --enumerate
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.17
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.10.10.37/ [10.10.10.37]
[+] Started: Fri May 28 13:04:16 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.10.37/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://10.10.10.37/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://10.10.10.37/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://10.10.10.37/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.8 identified (Insecure, released on 2017-06-08).
| Found By: Rss Generator (Passive Detection)
| - http://10.10.10.37/index.php/feed/, <generator>https://wordpress.org/?v=4.8</generator>
| - http://10.10.10.37/index.php/comments/feed/, <generator>https://wordpress.org/?v=4.8</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://10.10.10.37/wp-content/themes/twentyseventeen/
| Last Updated: 2021-04-27T00:00:00.000Z
| Readme: http://10.10.10.37/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 2.7
| Style URL: http://10.10.10.37/wp-content/themes/twentyseventeen/style.css?ver=4.8
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.10.37/wp-content/themes/twentyseventeen/style.css?ver=4.8, Match: 'Version: 1.3'
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:45 <==========================================================================================================> (350 / 350) 100.00% Time: 00:00:45
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:05:13 <========================================================================================================> (2575 / 2575) 100.00% Time: 00:05:13
[i] No Timthumbs Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:17 <===========================================================================================================> (137 / 137) 100.00% Time: 00:00:17
[i] No Config Backups Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:08 <=================================================================================================================> (71 / 71) 100.00% Time: 00:00:08
[i] No DB Exports Found.
[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)
Brute Forcing Attachment IDs - Time: 00:00:12 <======================================================================================================> (100 / 100) 100.00% Time: 00:00:12
[i] No Medias Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:03 <============================================================================================================> (10 / 10) 100.00% Time: 00:00:03
[i] User(s) Identified:
[+] notch
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://10.10.10.37/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Notch
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Fri May 28 13:11:21 2021
[+] Requests Done: 3292
[+] Cached Requests: 10
[+] Data Sent: 896.032 KB
[+] Data Received: 1012.446 KB
[+] Memory used: 270.102 MB
[+] Elapsed time: 00:07:04
Running dirbuster on 10.10.10.37
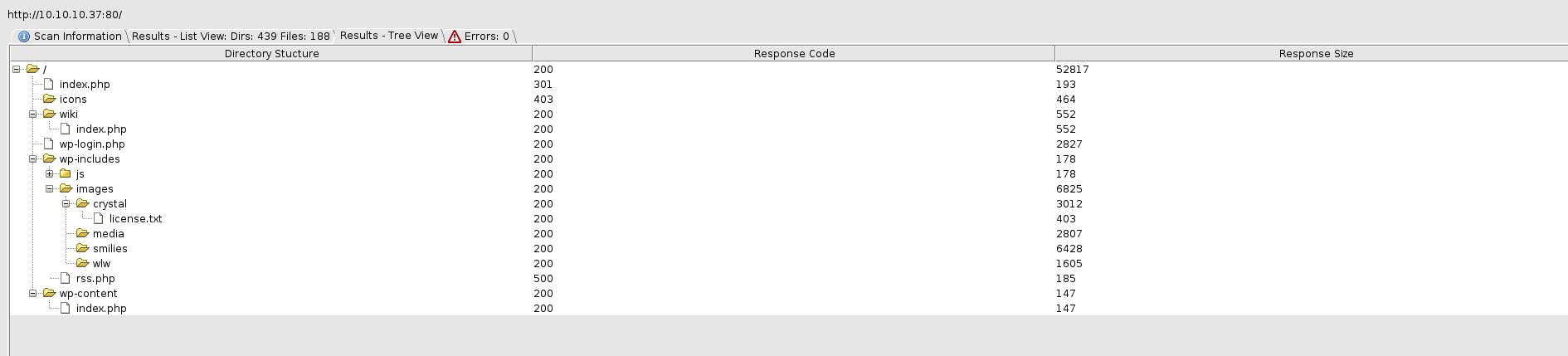
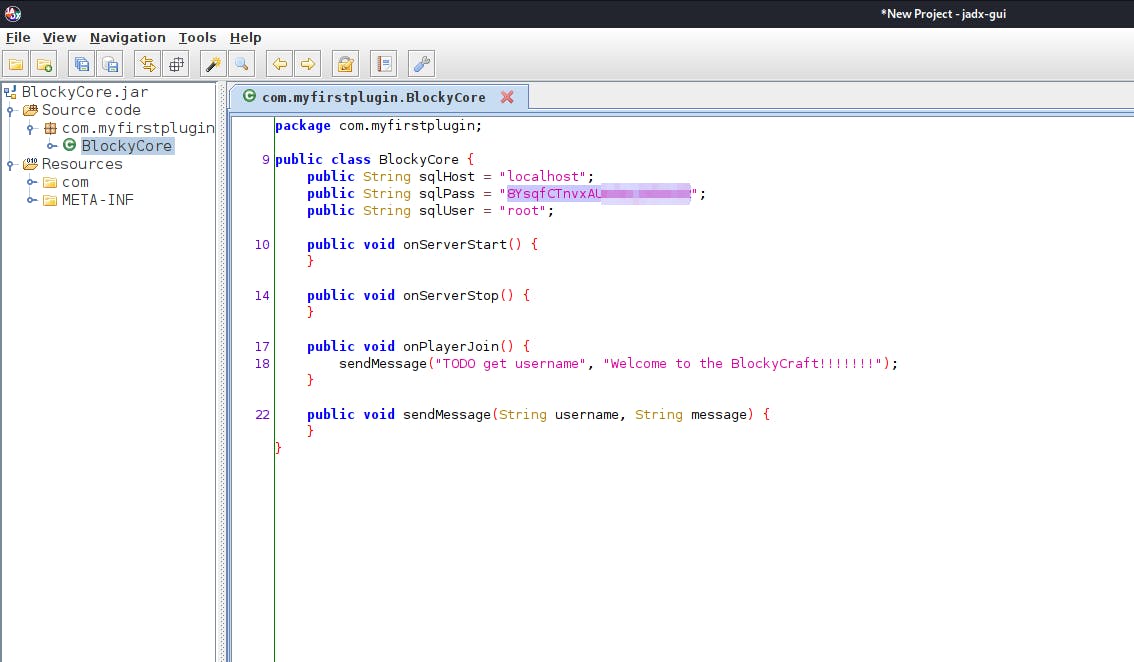
Going to /plugin we get a BlockyCore,jar file
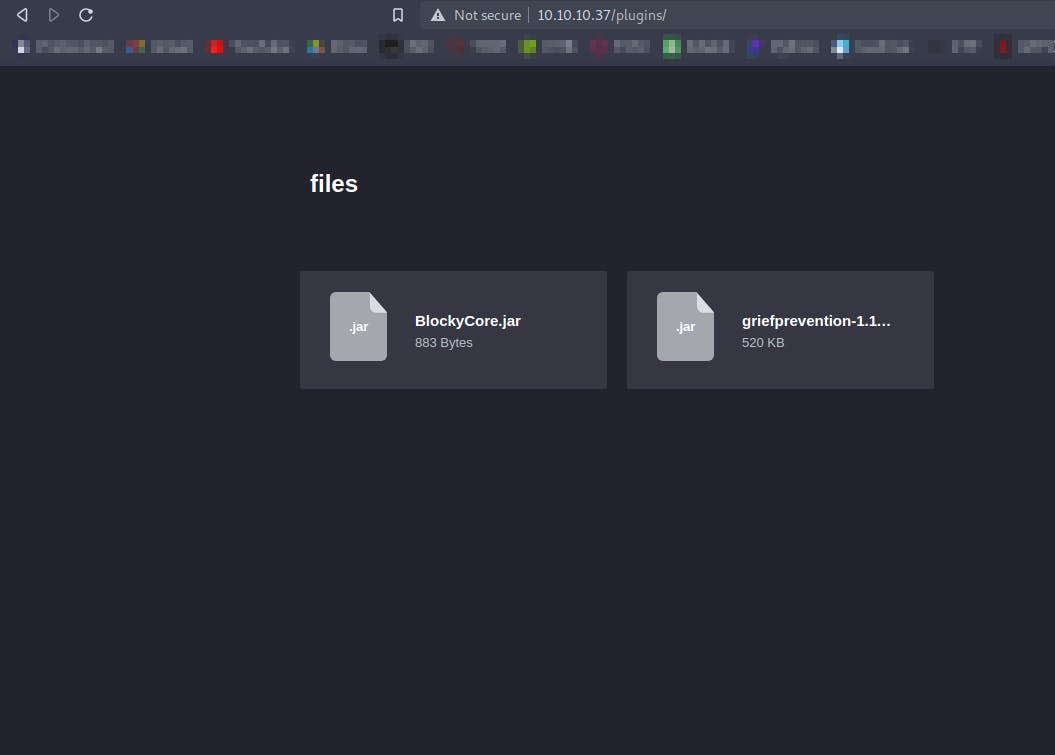
Using the jdax-gui to decomplie the .jar file we get that there is a file BlockyCore in the my-first-plugins which has the credentials for the sql user
Trying the username and the password in ssh login
The password doesn't work with the root user
Trying the user we got earlier in the wpscan
username : notch password : 8YsqfCTnvxA**
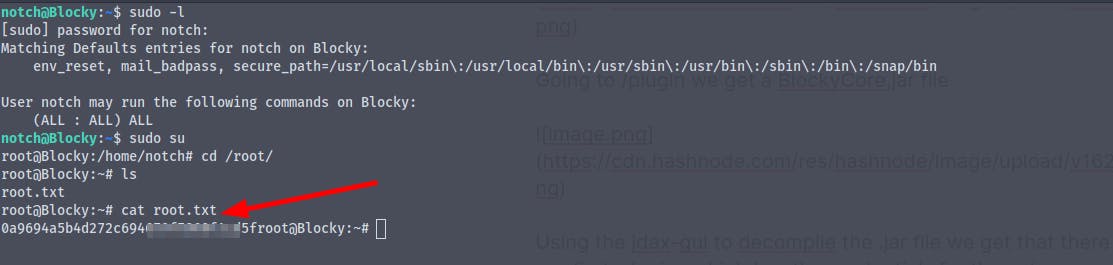
And we have successfully logged in as the user notch
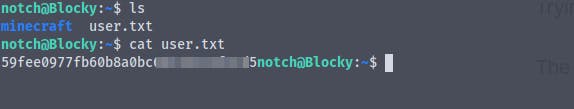
We now have the user flag
Now is the time for privilege escalation
We can see that the user notch can run all the commands as super user
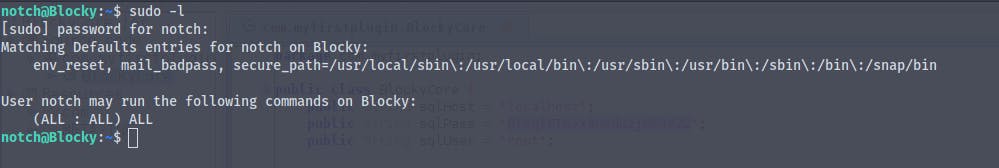
running sudo su we are now root and we get the root flag